March Newsletter - Vault now in Beta
Pranav Shikarpur
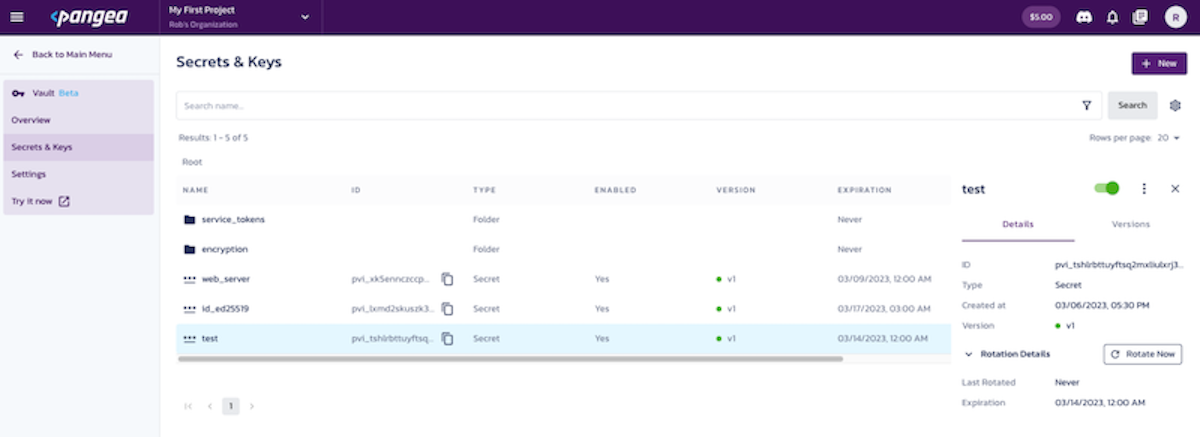
We have a new service announcement to make!!! Vault - our secret and cryptographic key store is available in Beta. The Vault service combines the best capabilities of key and secrets management solutions into one service. It enables you to generate, import, and manage key lifecycles while also providing endpoints for performing cryptographic operations without ever exposing private key material. Similarly, the Vault service allows you to store, manage, and access secrets as text strings.
Using the Vault service helps ensure a secure development lifecycle by preventing private key material from ever being leaked into code and preventing the accidental hard-coding and exposure of secrets.
Learn more about how you can use Vault to better secure your secrets and keys.
Product Updates

Digital Element (DE): We’re excited to announce our partnership with Digital Element and the release of four new Intelligence Services! The services will initially be in Beta then released to General Availability (GA) in a couple of weeks.
The services include:
Geolocate: Pinpoint users’ geographic location from just their IP address, and uncover other actionable insights like demographic data and connection type. Accuracy rates of 99.99% at a country level, 98%+ at a regional level, and 97%+ at a city level – globally. Coverage of 99.9999% of all seen IP addresses worldwide and works even for devices with GPS turned off. DE takes IP-based location targeting to the next level by combining traditional infrastructure analysis, insights gleaned from a network of global commercial partners, and location intelligence provided from mobile devices and billions of real-time data signals.
Domain: Resolve an IP to its domain. The domain database is an accurate representation of domain names for IP addresses. With patented domain name expansion and injection algorithms DE have been able to increase the number of IPs associated with domain names.
Proxy Detect users connecting through a proxy. DE’s industry-leading proxy data is gathered via their unique proxy analyzer, which combs alleged proxy lists and stores the data for analysis. IP addresses are constantly evaluated and re-evaluated to see if they exhibit proxy-specific behavior, such as requiring login credentials.
VPN Detect users connecting through a VPN. VPN Proxy database provides additional insights around the proxy hosts identified as either VPN or DNS within our Proxy Identification database. This database also highlights the individual IP address tied to the VPN or DNS proxy.)
Introduce tenant_id as a field in Audit Schema - we now support multi-tenancy capabilities for Secure Audit Log. Learn how to separate log entries by their Tenant IDs.
Operational Status - Did you know you can subscribe to status updates and review past incidents with our status page.
Trust Center - We also continuously monitor our overall security posture - Infrastructure Security, Network Security, Data Security, Product Security, App Security and Organization Security. Compliance is a priority for Pangea, and we want to give you visibility into it.
Pangea's Equator
Integrating Pangea Audit log and File Intel with Python Django
In this tutorial, learn how to integrate Pangea’s Secure Audit Log and File Intel. Using these services you can log important user activity like authentication logs into Secure Audit log and check if a file is malicious using the File Intel Service. Start building.
redact(), quack quack
Personal Identifiable Information(PII) theft seems to be in the news daily, but PII should also be considered in other scenarios to prevent over or inappropriate sharing with gig workers or young users on your app. Learn more on how Redact can mask profanity. Read more!
Install the Critical Document Auditing Extension in Firebase
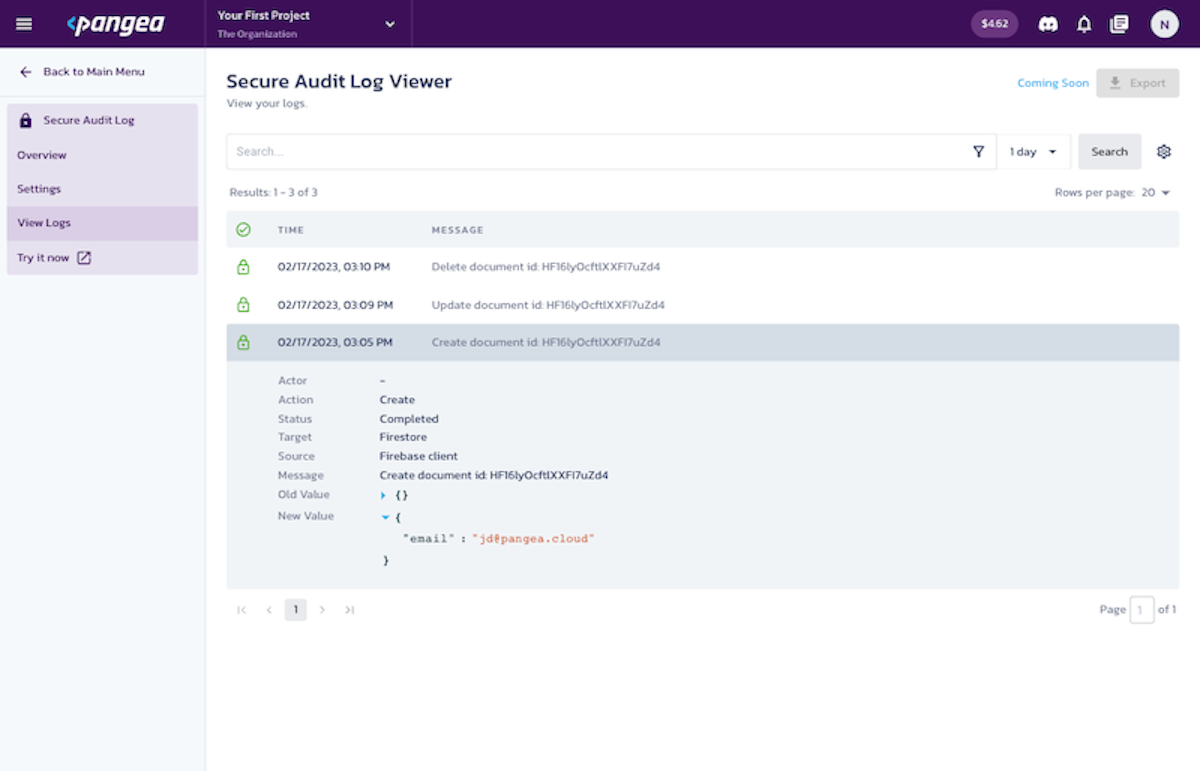
In this tutorial, you’ll learn how to monitor compliance-critical or sensitive collection of documents in Firestore and record updates made to those documents on a tamper-proof audit log. Learn more.
Events

We’re thrilled to announce that Pangea has been named one of the top 10 finalists in the 2023 RSA Innovation Sandbox at RSA Conference. On Monday, April 24, Founder and CEO Oliver Friedrichs will present to a panel of industry judges and a live in-person audience at RSA Conference 2023 in San Francisco. Read more.

Join our CMO Grace Francisco on April 27th as she discusses what Left of Left security is for developers building apps in her keynote at WITS Northeast.
For all events, visit our news and events page
We’re growing. Here are some roles we are hiring for!
For more openings, view our careers page!
That’s it for March!

Little community announcement to make, we’re moving our community to Slack. We look forward to seeing you there.
Visit our documentation for more starter guides and to learn how to secure your next application using Pangea.
Follow us on Twitter and join our community Slack channel. We have a team of developers ready to help support your next project and answer any questions you have.
More Articles
Services
Case Studies
Use Cases


