Overview
Infrastructure automation projects frequently involve including and managing user credentials, user ids, telephone numbers, and email addresses for both employees and often for external business contacts. Identifying if the user account information was previously breached can improve the security posture during onboarding.
Where is Personally Identifiable Information (PII) Used?
Network device configurations (routers, switches, and firewalls) require selecting and applying passwords for services enabled on these devices.
When deploying site-to-site VPNs, associated routing protocol authentication between devices (routing protocol authentication, pre-shared keys (PSK) for an IPSec) are also specified and should be re-provisioned periodically.
For example, a Network Source of Truth, such as NetBox Labs, may involve creating user accounts (usernames, email addresses, and phone numbers for the contact database to specify a person with a circuit, site, site groups, and locations).
A recorded webinar on securing credentials used on device configurations as part of the network automation process is available on the Programmability and Automation Meetup channel.
Let’s examine how an organization's security posture can be improved as users are added to the internal databases of systems like NetBox Labs or the Cisco Unified Communications Manager.
Automation of business functions
The Cisco Unified Communications Manager (Call Manager) has been prominent in large and small organizations for over 25 years. To operate, it requires a SQL database to manage both the configuration of the system and the directory (phone) numbers of the users. The end user table contains entries for user id, phone number, email address, and first/last name.
The table can be managed from the Graphical User Interface (GUI), but also through an Application Programming Interface (API). The optimal solution is onboarding and offboarding students, faculty, and employees as an integrated workflow invoked from an IT Service Management (ITSM) system.
Event-Driven Workflow
Red Hat Ansible Automation Platform has a certified integration for ServiceNow ITSM and in Ansible Automation Platform 2.4 an event plugin is also supported.
Automating the user onboarding process, initiated from ServiceNow, is one means by which Event Driven Ansible can monitor activity, and rapidly invoke the automation to provision the user in the user database in Cisco Unified Communications Manager (Call Manager). The workflow is completed by updating the ServiceNow ticket with the result of the Call Manager provisioning.
Security as a Service
Pangea is a Security Platform as a Service (SPaaS) you can leverage with simple API calls for authentication, audit logging, secrets management, sensitive data removal, and intelligence services.
Pangea was founded to incorporate API-first security services for developers, not just front-end developers, but also for infrastructure automation as well. Pangea provides a Python library Software Development Kit (SDK) and support for other popular programming languages. To enable developers, creating an account on the Pangea portal (console) is as easy as authenticating using GitHub as your identity provider. This account is pre-funded, enabling access to the API, SDKs, documentation, and access to the Slack support channel. It provides a low barrier to entry for application developers
Ansible Content Collection for Pangea
Ansible Content Collections uses a standardized directory structure for packaging documentation, metadata, playbooks, roles, tests, and module plugins for an automation solution. BlueAlly developed a private content collection for a client’s Call Manager automation.
BlueAlly also developed a public Ansible Content Collection for these Pangea services:
User Intel - determines if an email address, username, phone number, password, or IP address was exposed in a security breach.
Domain Intel - retrieves intelligence about known domain names, providing insight into the reputation of a domain.
URL Intel - retrieves intelligence about the reputation of a URL.
This collection is available for download from Ansible Galaxy under the
NetCraftsmen namespace:
https://galaxy.ansible.com/ui/repo/published/netcraftsmen/pangea/
Incorporating security checks when provisioning users
The Cisco Unified Communications Manager (Call Manager) workflow automation use case is an example where an Ansible Content Collection providing playbooks and plugins to automate the adds, updates, and deletion of users from the Call Manager database is augmented to include security checks as part of the user provisioning.
Security checks can easily be added to the Call Manager solution, including a Pangea User Intel check on the email address, username, and phone number as part of the student, faculty, or employee onboarding process.
This is accomplished by creating an access token on the Pangea Cloud portal and incorporating the Pangea plugin module into the Call Manager Ansible automation playbook.
A diagram of the revised workflow follows:
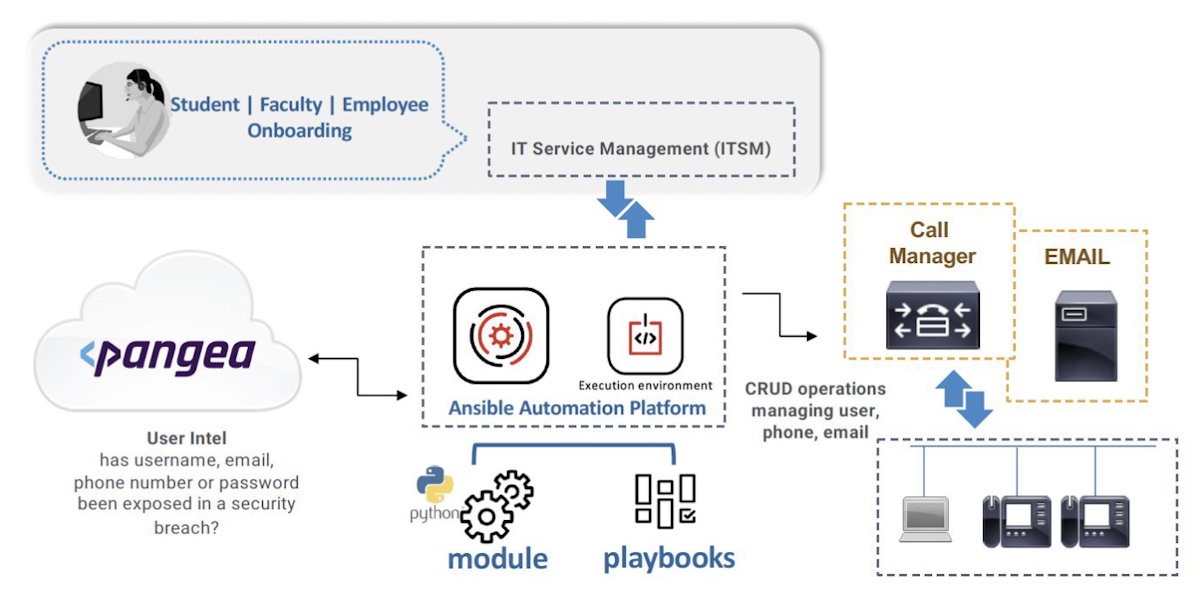
Because the ITSM system has captured the name, user id, and email for provisioning the directory number, incorporating a breach user check is a simple process.
The value of identifying breached users
Let’s examine a real-world example of how breached users may potentially compromise a faculty member of a university. Faculty and students often use the same, or similar usernames, on multiple email accounts.
Many colleges and universities enable public search functionality for staff, faculty, and students. We selected one faculty member from the school’s public search web page and used the Pangea User Intel function to determine if the username portion of the university email domain was compromised.
In this example, the Pangea User Intel search returned 7 breach occurrences from SpyCloud, a dark web database, one identified an exposed plain text password.
country_code: US
domain: rr.com
email: <REDACTED>@cinci.rr.com
email_domain: cinci.rr.com
email_username: <REDACTED>
ip_addresses: [<REDACTED>]
password: <REDACTED>
password_plaintext: <REDACTED>
password_type: sha1
record_cracked_date: '2020-10-05T00:00:00Z'
record_modification_date: '2020-10-05T00:00:00Z'
salt: <REDACTED>
severity: 20
source_id: 13916
spycloud_publish_date: '2018-03-20T00:00:00Z'
username: <REDACTED>
The details are redacted; however, this faculty member’s username was reused in the @cinci.rr.com personal email account, and that account is compromised.
It is common for people to reuse passwords on multiple accounts. When onboarding students, faculty, and employees, the onboarding process should incorporate a breached user check using the Ansible Content Collection for Pangea Cyber.
Identifying personal, or past business, phone numbers, user ids, and email addresses exposed in breaches provides valuable information in the onboarding process to prevent compromising the newly created accounts.
Summary
BlueAlly developed and published the Ansible Content Collection for Pangea to enable the automation community to incorporate security checks into workflow and infrastructure automation projects in a simple and consistent interface.
For additional information on this or other BlueAlly solutions, reach out by email at contact@blueally.com or the contact page at www.blueally.com/contact.




