
Rob Truesdell
VP, Products
Product Updates - June 23, 2023
Redact
Redact with Hashing
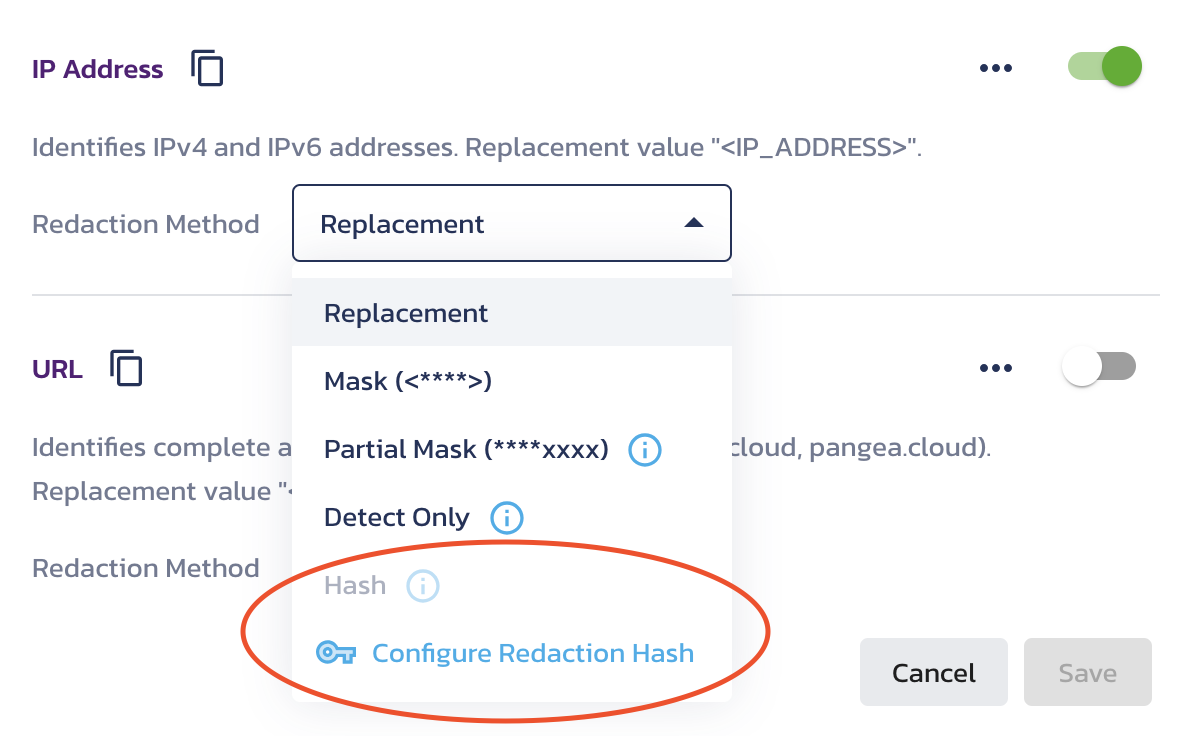
With the Redact API, you can now generate a hash derived from the redacted text (with a salt) to use as the text replacement in the string. The salt used with the hash is stored in the Vault service. This functionality allows you to identify recurring patterns in the strings being redacted without ever exposing or identifying the original characters that were redacted. It’s very useful for a wide variety of security monitoring use case cases.
Secure Audit Log
Multi-config Support
Multi-config support allows you to manage multiple configurations of the Secure Audit Log service within the same Pangea Project. This now puts more importance on specifying a config ID in the input parameters of any Secure Audit Log API call - in both the SDKs, REST APIs, or in the documentation page. Therefore don’t forget about the config ID parameter if you’re managing multiple configurations! If you only have one config, then there is no need to specify an ID.
IP Intel
Team CYMRU data source is GA
Team Cymru is a threat intelligence pioneer, and their data powers many security vendors’ offerings. In addition to a global network of sinkholes, honeypots, darknets, and sensors, they work with ISPs, hosting providers and over 130 CSIRT teams across 86+ countries to make the Internet a safer place. Team CYMRU observes activity across every ASN on the Internet and scores that activity to bring you unparalleled threat intelligence. Their IP Reputation Feed gives a complete 10 category breakdown as well as a risk score for a given IP which is calculated using additional pattern data:
| Bot | Talking with a botnet |
| Bruteforce | Attempting brute force SSH logins |
| Controller | Being used to control botnets |
| Darknet | Scanning dark IP space for vulnerable hosts |
| Honeypot | Interacting with a honeypot |
| Openresolvers | An open DNS resolver |
| Phishing | Hosting a phishing webpage |
| Proxy | Used as a proxy to connect to the public Internet |
| Scanner | Associated with network or service scanning activity |
| Spam | Sending spam email |
To read more about the power of Team CYMRU’s intelligence, check out this blog.
SDK Updates
Java
The Java SDK has been released and has full support for all services.
C#
Secure Audit Log now can be used via the C# SDK. More services will support the C# SDK over the coming weeks.
Console
Terms of use updated
For all of your legal experts out there, and everyone else, feel free to review our terms of use at your leisure.