When I say “secure authentication,” what comes to mind?
You probably think of SSL, password policies, and MFA. Those are a good starting point but what if we could look into the authentication request itself? What if we could use that request context - the IP address, geolocation, and even the user’s information - to apply additional security in front of our application in real-time?
With that in mind, I'm excited to announce that we’ve embedded our threat intelligence capabilities directly into the Pangea AuthN service.
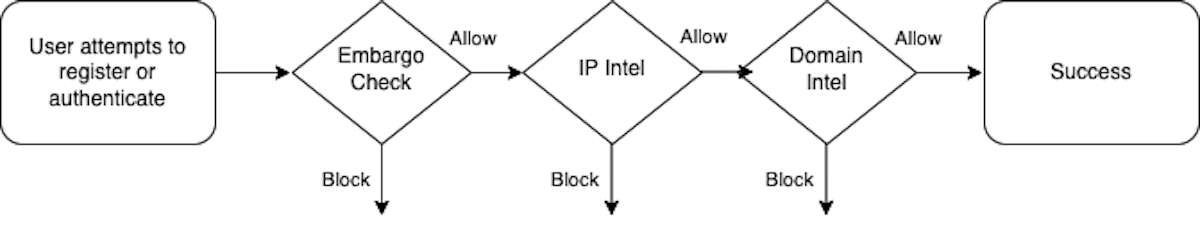
Now you can detect and block bad actors long before they’re in your system. For this release, we implemented three of our key services: Embargo, Domain Intel, and IP Intel.
What is Threat Intel?
Within Pangea AuthN, the Embargo service performs a geolocation check on inbound requests, applies a policy lookup against international sanction rules like ITAR, EAR, OFAC, and then allows or blocks the request. Further, you can customize your filters in case you see fraud or bad actors from other countries.
Then we’ve layered in the IP Intel service to identify and resolve IP reputation, VPNs, and proxies. We can help you identify and block botnet traffic, suspicious nodes, and otherwise bad actors and systems when they attempt to access your system.
Finally, we added our Domain Intel service to block the temporary, garbage, or spam domains at registration time. Now your email confirmations, shipping notices, and even marketing campaigns are going to legitimate users and not disappearing into the void and damaging your own domain’s reputation.
How does Threat Intel in AuthN work?
Behind the scenes at Pangea, we opened the AuthN user registration and authentication flows to plug in each of these components. These components call the other services, return to the flow, and it makes a simple Allow/Block decision.
Further by dividing user registration and authentication into separate flows, you can apply different rules depending on your requirements. For example, you may reject registrations from specific countries but if an existing user visits that country, they can still authenticate.
Overall, these services come together into a pipeline with configurable Allow/Block rules:
We also realize that you may want to do more and add your own rules. While we don’t support that in the pipeline currently, we take all the collected context - IP reputation, geolocation, VPN status, proxy identification, domain reputation, and more - embed them into the JWT, and pass it back to your application. If you want to put suspicious users into a different group, limit their access, or even tune an experience based on their country of origin, you have all the information you need.
Why does Threat Intel matter?
According to many sources, bots make up well over 50% of web traffic as a whole and then we have bad actors trying to compromise our systems and users’ accounts. In the best case, it's an irritating and unnecessary load on our systems. In the worst case scenarios, these bots and bad actors spam forums, harass our users, and defraud our businesses.
By using geographic, IP, and domain context during authentication, we can mitigate fraud and spam, reduce the load on our systems, and focus on the features that matter to our customers instead of chasing IP block ranges, domain filters, and cleaning up the mess when we miss. Now instead of spending time learning new tools, rearchitecting our apps, and wiring in new components, you can activate strong controls with a few clicks.
At Pangea, we measure security features in seconds, not story points.
Using Pangea Threat Intel with AuthN
If you’re already using our AuthN Hosted Flow, you can turn these services on and use them immediately. Log into the Pangea User Console, select your project, and visit Settings > Security Controls to enable the services you need. It should take less than 10 seconds.
If you’ve built your own Authentication process using our AuthN Flow APIs, you can already embed any of the services and rules directly on your own.
How much does AuthN and Threat Intelligence cost?
Your first 5,000 monthly active users (MAUs) and $5 monthly credit are still included for free.
Once you activate your threat intelligence options, you will be billed at our normal rates per request. Remember that user registration and authentication are separate so you can dial up or down the constraints depending on your needs. For more detailed information on billing, check out our Pricing and Billing Details pages.
What’s next for AuthN?
AuthN’s future comes down to this diagram because there’s power in a pipeline.

Now that we’ve split the process into a state machine, we can embed new capabilities like new checks, custom checks, or even states beyond the simple Allow/Reject. This gives us a whole world of capabilities but we’d love to hear from you:
What else would you like to check?
What rules do you want to see?
What workflows should this initiate?
What frameworks and tools do you build with regularly?
Visit us in our Pangea Builders Slack to let us know and even get early access to products and features.
Or sign up and get started with MFA, Social Auth, your first 5,000 monthly active users and $5 monthly threat intel credit for free!



