Check a domain
Check the source domain of your app’s users using Domain Intel
The code samples below were created using the Pangea SDKs, which are open-source on GitHub:
Introduction
Check for malicious domains on your app
Create a token
Expand for details
Create a token so that you can access the Domain Intel endpoints:
- Go to the Pangea Console and click Domain Intel in the left-hand navigation menu. The Domain Intel Overview page will appear.
- On the Domain Intel Overview page, you'll see a notification asking you to set a service token. Click Create new token toward the bottom right side of your screen.
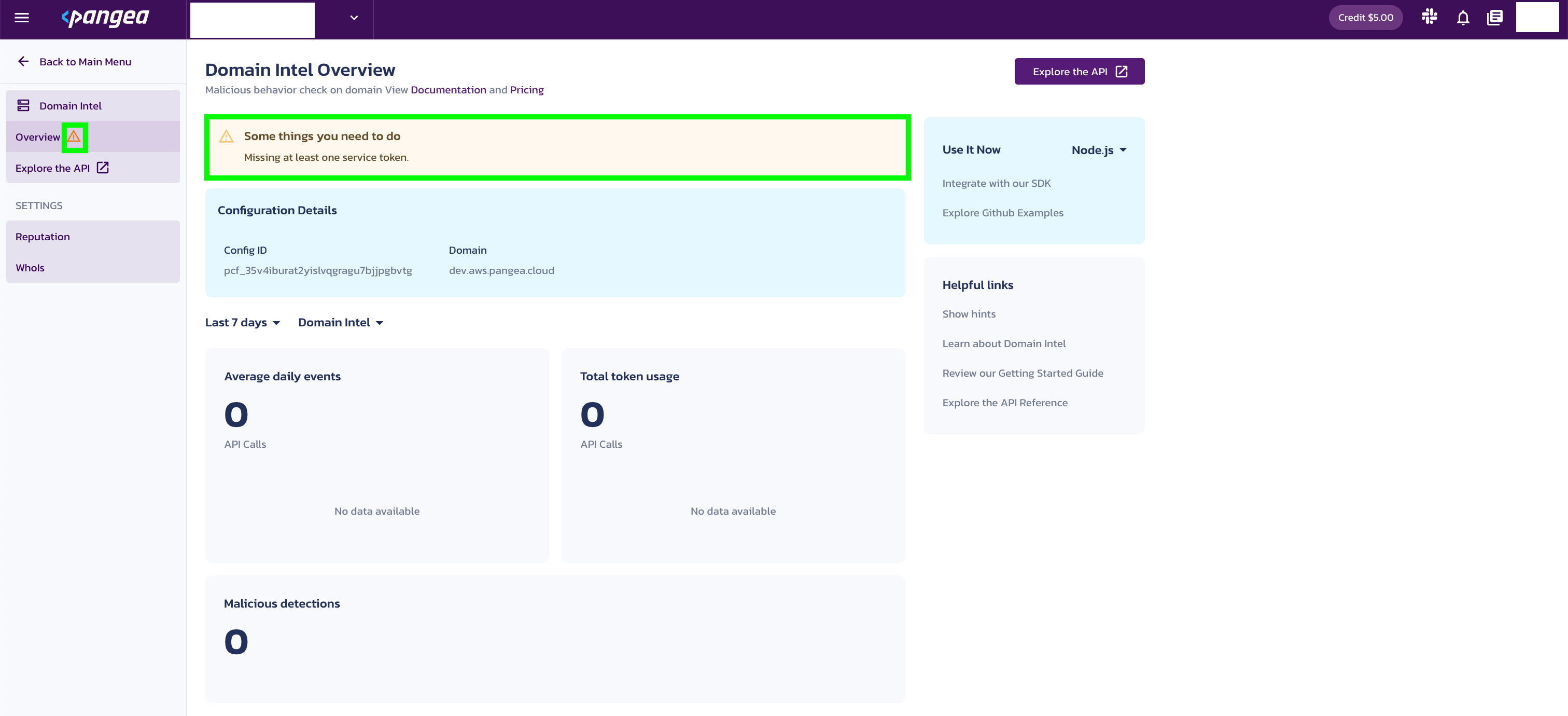
- You’ll be prompted to create a token. Enter a Token name and select an Expiration Date. You may also create a token for all Intel services, if you wish.
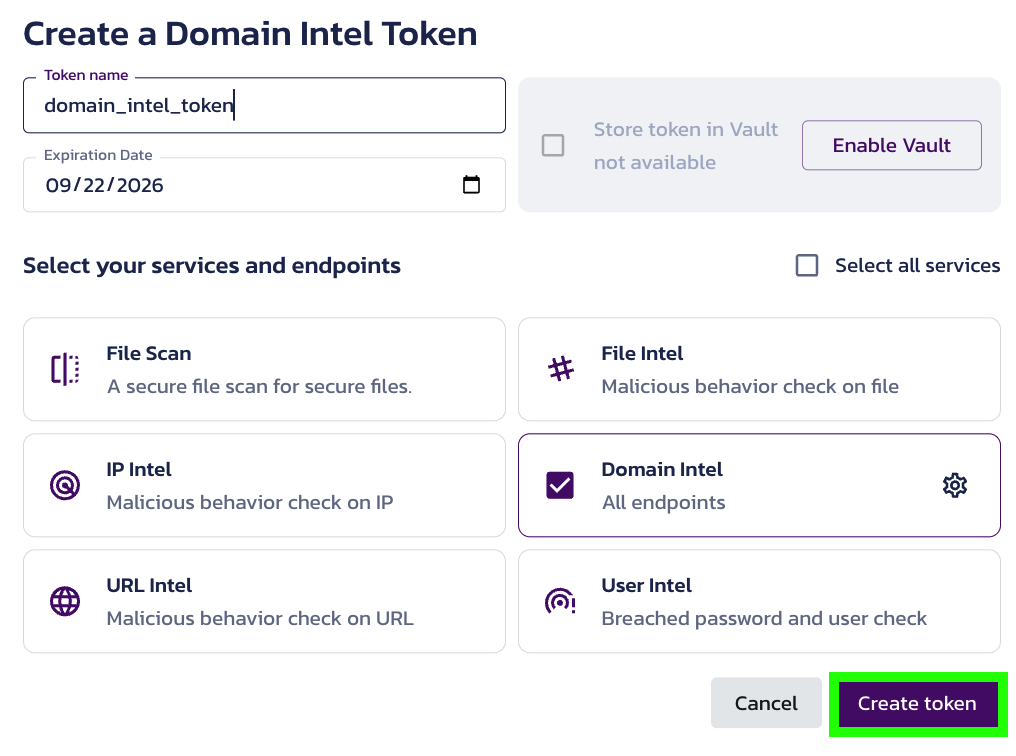
- Once configured, the token is available in the Tokens section of the File Intel Overview page.
Select a provider as default
Expand for details
Providers can be selected as default in the Pangea Console . Setting a provider as default in the Pangea Console means your API request calls will use this provider, unless another provider is specified as part of your API request.
To select a provider as default for an API:
- Go to the Pangea Console
- On the left-hand navigation menu, select Domain Intel
- Go to Settings
- If you select Reputation then switch on Default for your preferred provider
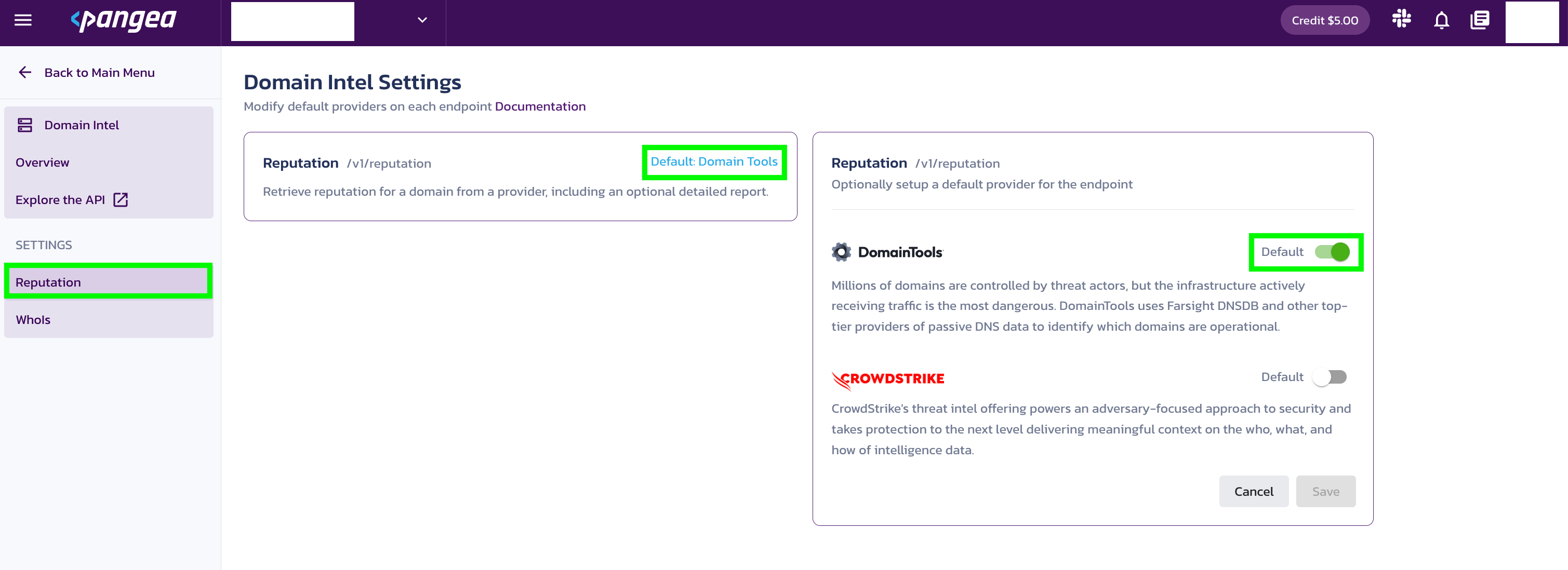
You can also select a provider and override the default provider by specifying their name in the provider field when making an API request to the /reputation endpoint. This is helpful if your default provider returns a verdict of Unknown and you want a second opinion from another provider.
- If you select WhoIs, the provider will be configured as WhoIs

Test the service
The interactive Domain Intel API Reference allows you to test API endpoints from the documentation. This is an easy way to play around with domains and providers to see what kind of data is returned.
Configure your app for communication with the Pangea service
For your app to communicate with the Pangea service, you must put the values of the following Configuration Details into the PANGEA_INTEL_TOKEN and PANGEA_DOMAIN environment variables:
tokendomain
These Configuration Details are created when you enable Domain Intel and can be found in the Overview section under Domain Intel.
Set environment variables
To set each variable in bash:
export PANGEA_DOMAIN="yourServiceDomain"
export PANGEA_INTEL_TOKEN="yourAccessToken"
Send client domain to Domain Intel service
A /reputation call from your app to the Domain Service might look like the sample below. You will notice:
- the environment variables from above are embedded in the sample below
rawis set totrueso the API response will contain a detailed report about the domain- the
providerfield is set todomaintools(if you set the default provider in the Pangea Console then this field is not required unless you’re trying to call another provider for a second opinion)
import os
import pangea.exceptions as pe
from pangea.config import PangeaConfig
from pangea.services import DomainIntel
token = os.getenv("PANGEA_INTEL_TOKEN")
domain = os.getenv("PANGEA_DOMAIN")
config = PangeaConfig(domain=domain)
intel = DomainIntel(token, config=config)
def main():
print("Checking domain...")
try:
response = intel.reputation(
domain="www.example.com",
provider="domaintools",
verbose=True,
raw=True,
)
print(f"Response: {response.result}")
except pe.PangeaAPIException as e:
print(f"Request Error: {e.response.summary}")
if e.errors:
for err in e.errors:
print(f"\t{err.detail}")
print("")
Domain Intel API sends a response
After your app submits a domain to the Domain Intel service, you will receive the following JSON response:
{
"request_id": "prq_d6qm5rwlc7sd4rh33vnso65kmanw5mj5",
"request_time": "2022-10-12T18:08:04.753Z",
"response_time": "2022-10-12T18:08:05.207Z",
"status": "Success",
"summary": "Domain was found",
"result": {
"data": {
"category": [
"sinkhole",
"proximity",
"threat_profile",
"threat_profile_phishing",
"threat_profile_malware",
"threat_profile_spam"
],
"score": 100,
"verdict": "malicious"
},
"parameters": {
"domain": "www.example.com",
"verbose": true,
"raw": true,
"provider": "domaintools"
},
"raw_data": {
"response": {
"domain": "www.example.com",
"risk_score": 100,
"components": [
{
"name": "sinkhole",
"risk_score": 100
},
{
"name": "proximity",
"risk_score": 23
},
{
"name": "threat_profile",
"risk_score": 89
},
{
"name": "threat_profile_phishing",
"risk_score": 81
},
{
"name": "threat_profile_malware",
"risk_score": 89
},
{
"name": "threat_profile_spam",
"risk_score": 35
}
]
}
}
}
}
In this instance, the verdict returned as malicious. Additional raw data (from the provider specified in the API request) was
returned.
Understand and review results
The API responses sent by the Domain Intel /reputation and /whois calls include various fields and values; however, the ones listed on the API response page gives you the most information about the disposition of a domain. To learn about more response fields, visit the Domain Intel API Reference.
Decide what to do with the domain
You decide how to respond and/or communicate with your users once a domain's reputation becomes evident. Here are some suggestions:
- Block the domain
- Validate the user of the suspicious domain with:
- CAPTCHA
- Multi-factor Authentication (MFA)
In this use case, the domain will be blocked and no message will appear for the user to avoid giving them any further hints.
Was this article helpful?