
Rob Truesdell
VP, Products
Product Updates - January 09, 2024
Authentication
Integration with Threat Intel
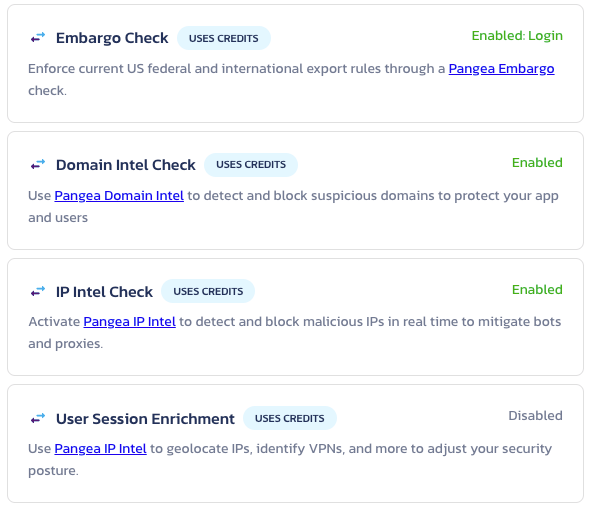
With this update of AuthN, we’ve embedded our threat intelligence services to give you fine-grained controls and protections for your applications and users. Internally, we implemented a pipeline using Embargo, IP Intel, and Domain Intel allowing you to accept or block users at registration time, authentication time, or both.
These options are entirely configurable via the Pangea User Console to transparently improve your application and user security without changing a single line of code. For allowed requests, we pass the entire connection, IP, and user context to your application for additional logging, user experience customization, or even policy enforcement.
Vault
Support for Quantum-safe Cryptographic signing algorithms
The following Dilithium and Sphincs algorithms have been implemented in Vault. Both are for signing purposes. You will now see them available in the console and docs:
ED25519-DILITHIUM2-BETA
ED448-DILITHIUM3-BETA
SPHINCSPLUS-128F-SHAKE256-SIMPLE-BETA
SPHINCSPLUS-128F-SHAKE256-ROBUST-BETA
SPHINCSPLUS-192F-SHAKE256-SIMPLE-BETA
SPHINCSPLUS-192F-SHAKE256-ROBUST-BETA
SPHINCSPLUS-256F-SHAKE256-SIMPLE-BETA
SPHINCSPLUS-256F-SHAKE256-ROBUST-BETA
SPHINCSPLUS-128F-SHA256-SIMPLE-BETA
SPHINCSPLUS-128F-SHA256-ROBUST-BETA
SPHINCSPLUS-192F-SHA256-SIMPLE-BETA
SPHINCSPLUS-192F-SHA256-ROBUST-BETA
SPHINCSPLUS-256F-SHA256-SIMPLE-BETA
SPHINCSPLUS-256F-SHA256-ROBUST-BETA
New Encrypt-Structured/Bulk Encryption API
There is a new Encrypt-Structured Vault API that can take a JSON document and a JSONPath spec that selects elements of the JSON to be encrypted. The functionality is similar to our Redact-Structured API. For example, using a JSONPath of
$.batch_input[*].ciphertext
with a JSON document like this:
{
"batch_input": [
{
"ciphertext": "{ssn_token_1}"
},
{
"ciphertext": "{ssn_token_2}"
}
]
}
Would return a JSON document where just the "{ssn_token_1}", and "{ssn_token_2}" elements of the document are replaced with their encrypted counterparts.
There is also a corresponding Decrypt-Structured Vault API.
Intelligence Services
Support for Bulk Queries
The File, IP, URL, Domain, and User Intel APIs now support bulk queries. There are new /v2 versions of these APIs that take an array of 1 to 100 items for queries instead of just a single item. When querying for a single item, the response is synchronous; queries for 2 or more items give a 202 response along with a request_id that can be used to poll for completion and the final result. See the Asynchronous API Responses documentation for more information on processing asynchronous requests.
File Scan
Support for Presigned URLs
The File Scan endpoint now supports the use of a presigned URL to specify a file to be scanned. The use of presigned URLs allows you to skip the upload step and point the File Scan API to a cloud location where you already have a file.
Redact
Redact Edge
The Redact data plane object can now be self-hosted by users through the use of Pangea Edge. Pangea Edge uses a helm chart to deploy Pangea Edge Service (such as Redact) to a kubernetes cluster, allowing customers to host Redact in their own infrastructure. When the Redact service is used with Pangea Edge, the data plane object must have connectivity to the Pangea cloud service for control plan synchronization.
Multi-config support
The Redact service now has the option of creating additional rulesets. A ruleset can be the default ruleset as part of a configuration, or a ruleset can be invoked directly via an input parameter to the API.
Privacy Policy
Updated Policy
Pangea’s privacy policy has been updated to inform users of how input parameters to Threat Intel API calls are logged in Pangea’s back-end, what portions of parameters are logged, what the logging is used for, and how long the data is retained.