Upload Files
Upload a file for the file scan service in action
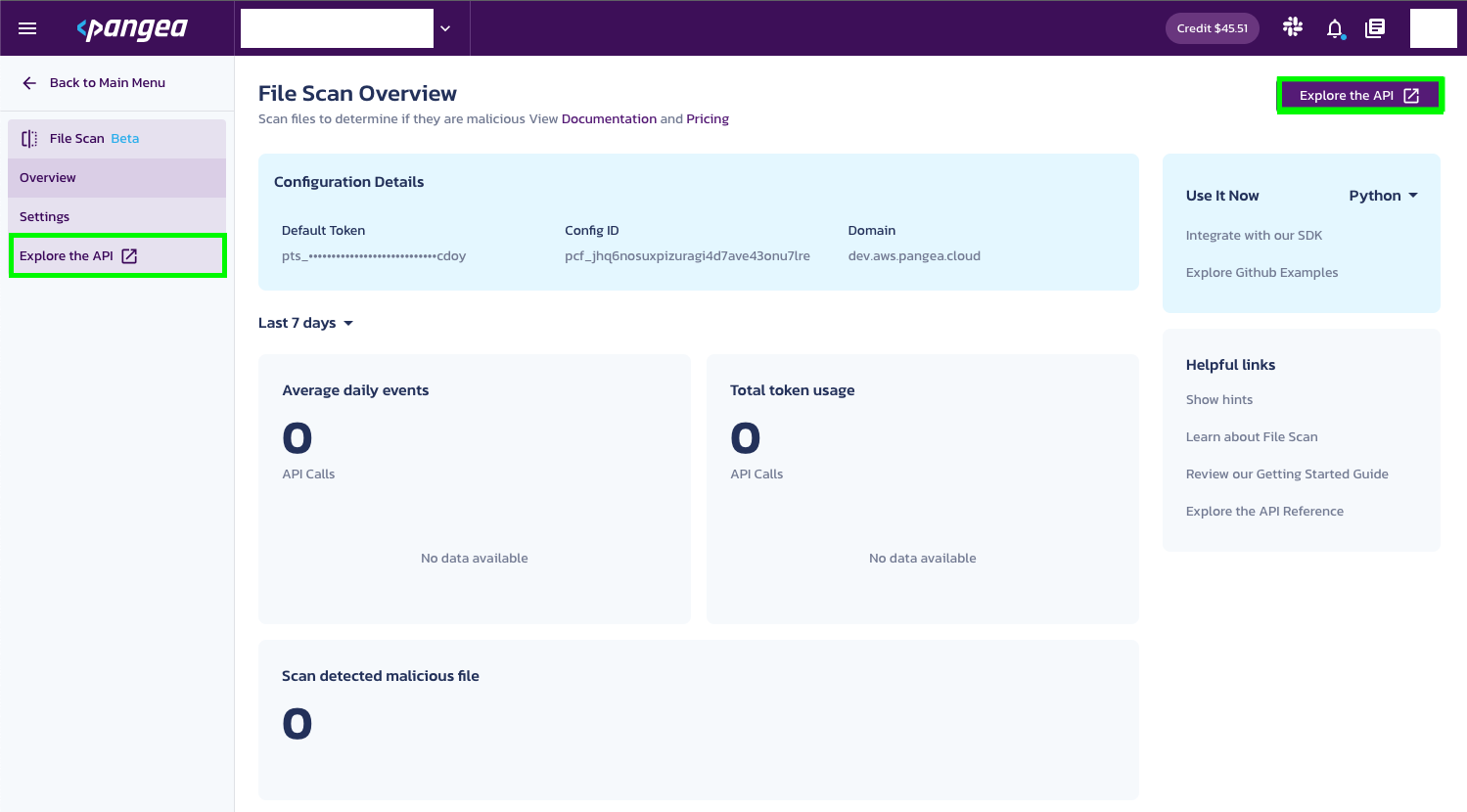
On the
Pangea Console , click the File Scan service to open its capabilities.From the File Scan service page, click Explore the API.
The maximum file size for File Scan is 500MB.
When using CrowdStrike as the provider, the File Scan service provides support for the following:
File types
- Portable Executable (PE)
- Mach object file (Mach-O)
- Executable and Linkable Format (ELF)
- Microsoft Office Word, Excel, and PowerPoint documents
- Portable Document Format (PDF)
- ZIP Archives (ZIP)
Architectures
- For PE: x86 and x86-64
- For Mach-O and ELF: x86, x86-64, arm, and arm64 (aarch64)
Now, the File Scan API Reference page opens for you to upload the file. You can upload the file by clicking on one of the following buttons:
- Upload
- Choose File
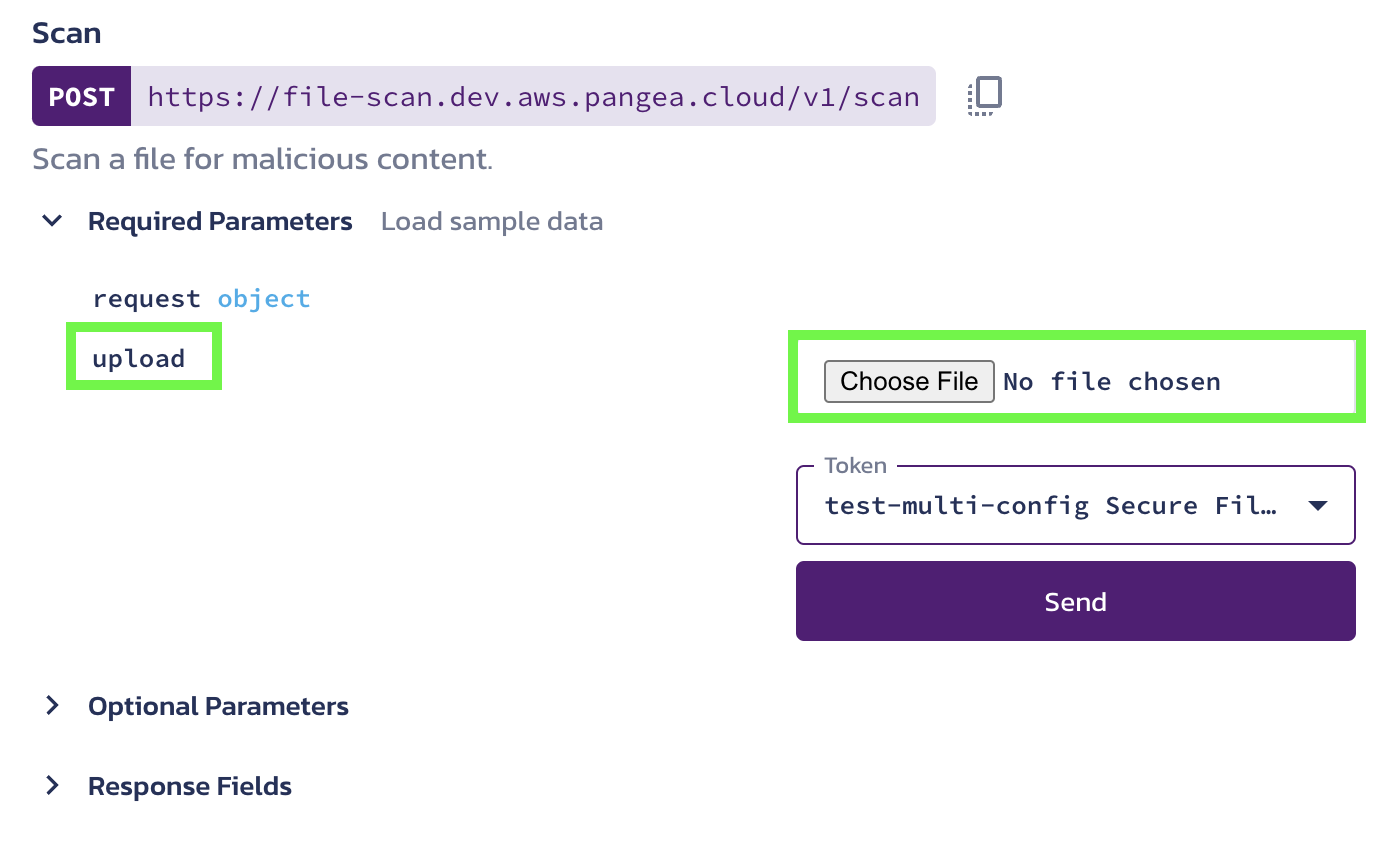
Click the Send button to upload the selected file for the Scan API to scan.
The request is generally asynchronous, and the response from the Scan API will be an HTTP 202 status response that includes request_id and summary fields with instructions to use the GET request to poll for the final result. With CrowdStrike as a provider, the response can be an HTTP 200 status that contains the scan result based on a reputation lookup.
The GET request interactive documentation is on the lower portion of the page, and it will be pre-populated with the correct request_id from the result of the Scan API call above.
Perform the post-request polling by setting the Poll Interval and clicking the Send button for the GET request.
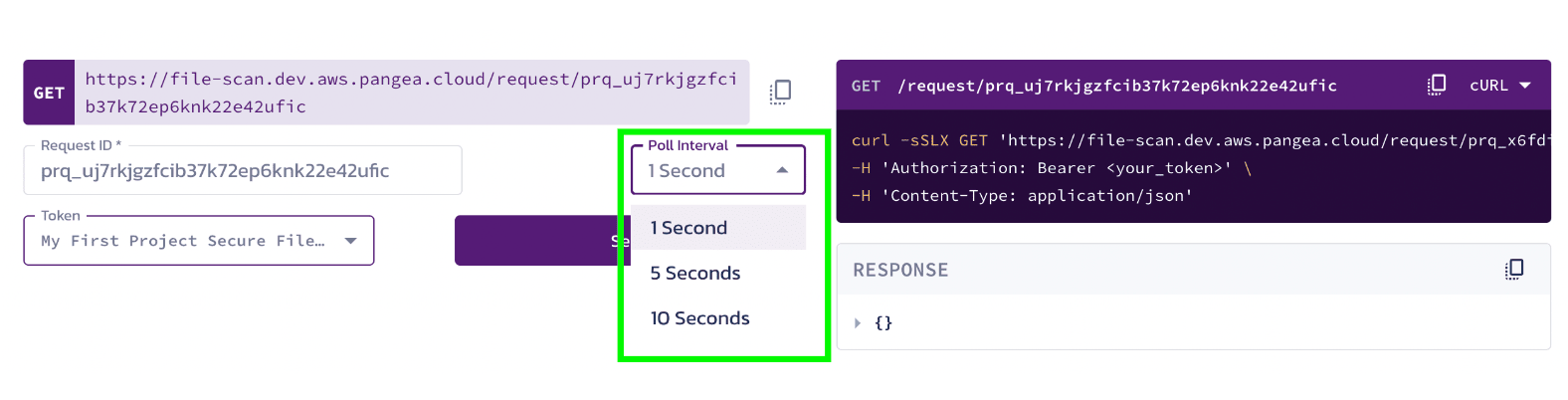
The RESPONSE will update on each polling interval until the final result is available.
Review intelligence report
Once the result is available, it will display in the window. The data will have the following information:
category: The type of malicious file, such as Trojan horse, virus, worm, etc.score: A numeric value between 0 and 100 that represents how malicious the file is perceived to be with 0 being benign, 1-99 being suspicious, and 100 as malicious.verdict: A verbal representation of the provider's view of the file's maliciousness. The verdict will be eitherbenign,unknown,suspicious, ormalicious.
If the scan contained the "raw":true flag, then the raw data will also be returned in the response.
Here are sample results of each scan type for each provider.
Sample CrowdStrike response
{
"request_id":"prq_t3dth3446nxef7o6sdcp53tq7xaumads"
"request_time":"2023-09-22T12:52:42.700409Z"
"response_time":"2023-09-22T12:52:43.973232Z"
"status":"Success"
"summary":"File was scanned"
"result":{
"data":{
"category":[
0:"pdf/malicious_confidence_90"
]
"score":80
"verdict":"suspicious"
}
}
}
Sample CrowdStrike raw response
{
"request_id": "prq_hax3bptpsycvhb4q4amjpyk7hd5axasy",
"request_time": "2023-09-22T12:53:17.131775Z",
"response_time": "2023-09-22T12:53:17.795978Z",
"status": "Success",
"summary": "File was scanned",
"result": {
"data": {
"category": ["pdf/malicious_confidence_90"],
"score": 80,
"verdict": "suspicious"
},
"raw_data": {
"reputation": {},
"scan": {
"ArchiveInfo": {
"clean_files": 0,
"dirty_files": 0,
"errors": 0,
"files_scanned": 0,
"potentially_unwanted_files": 0
},
"confidence": "medium",
"detection_name": "pdf/malicious_confidence_90",
"prediction": "malicious"
}
}
}
}
Sample ReversingLabs response
{
"request_id": "prq_bz4unnxextcq24zonv4ei7blhcbvnkfm",
"request_time": "2023-09-22T13:00:21.124944Z",
"response_time": "2023-09-22T13:10:29.382337Z",
"status": "Success",
"summary": "File was scanned",
"result": {
"data": {
"category": ["DOS.Malware.EICAR"],
"score": 100,
"verdict": "malicious"
}
}
}
Sample ReversingLabs raw response
{
"result": {
"data": {
"category": ["Text.Format.EICAR"],
"score": 100,
"verdict": "malicious"
},
"parameters": {
"verbose": true,
"raw": true,
"provider": "reversinglabs"
},
"raw_data": {
"info": {
"statistics": {
"file_stats": [
{
"type": "Text",
"subtype": "None",
"count": 1,
"identifications": [
{
"count": 1,
"name": "EICAR:Generic"
}
]
}
]
},
"file": {
"file_type": "Text",
"file_subtype": "None",
"size": 69,
"entropy": 4.910999957023231,
"hashes": [
{
"name": "md5",
"value": "69630e4574ec6798239b091cda43dca0"
},
{
"name": "rha0",
"value": "cf8bd9dfddff007f75adf4c2be48005cea317c62"
},
{
"name": "sha1",
"value": "cf8bd9dfddff007f75adf4c2be48005cea317c62"
},
{
"name": "sha256",
"value": "131f95c51cc819465fa1797f6ccacf9d494aaaff46fa3eac73ae63ffbdfd8267"
}
]
},
"identification": {
"success": true,
"name": "EICAR",
"version": "Generic",
"author": "ReversingLabs"
}
},
"classification": {
"propagated": false,
"classification": 3,
"factor": 5,
"result": "Text.Format.EICAR",
"scan_results": [
{
"ignored": false,
"type": "internal",
"classification": 3,
"factor": 5,
"name": "TitaniumCore Format",
"version": "4.1.0.0",
"result": "Text.Format.EICAR",
"rca_factor": 10
},
{
"ignored": false,
"type": "av",
"classification": 3,
"factor": 1,
"name": "Antivirus (based on the RCA Classify)",
"version": "2.82",
"result": "DOS.Malware.EICAR",
"rca_factor": 6,
"properties": [
{
"name": "scannerCount",
"value": "26"
},
{
"name": "scannerMatch",
"value": "26"
},
{
"name": "vendorCount",
"value": "18"
},
{
"name": "vendorMatch",
"value": "18"
},
{
"name": "firstSeen",
"value": "2011-06-18T08:21:00"
},
{
"name": "lastSeen",
"value": "2023-03-29T20:45:24"
}
]
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "ahnlab",
"result": "[VIRUS] Virus/EICAR_Test_File",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "ffri",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "avast",
"result": "EICAR Test-NOT virus!!!",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "bitdefender",
"result": "EICAR-Test-File (not a virus)",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "carbonblack",
"result": "virus",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "clamav",
"result": "Eicar-Signature",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "crowdstrike",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "crowdstrike_online",
"result": "malware.confidence_100",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "endgame",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "mcafee_beta",
"result": "EICAR test file",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "fireeye_online",
"result": "EICAR-Test-File",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "fortinet",
"result": "EICAR_TEST_FILE",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "gdata",
"result": "EICAR-Test-File (not a virus)",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "ikarus",
"result": "EICAR-Test-File",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "k7computing",
"result": "EICAR_Test_File",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "malwarebytes",
"result": "EICAR-AV-Test",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "mcafee",
"result": "EICAR test file",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "sentinelone_online",
"result": "DFI - Malicious COM",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "microsoft",
"result": "Virus:DOS/EICAR_Test_File",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "mcafee_online",
"result": "EICAR test file",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "microsoft_online",
"result": "Virus:DOS/EICAR_Test_File",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "panda",
"result": "EICAR-AV-TEST-FILE",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "panda_online",
"result": "EICAR-AV-TEST-FILE",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "quickheal",
"result": "EICAR.TestFile",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "rising",
"result": "EICAR-Test-File",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "rising_online",
"result": "EICAR-Test-File",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "antivir",
"result": "detected",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "sonicwall",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "sophos_susi",
"result": "EICAR-AV-Test",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "symantec",
"result": "EICAR Test String",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "symantec_beta",
"result": "EICAR Test String",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "symantec_online",
"result": "EICAR Test String",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "trendmicro",
"result": "Eicar_test_file",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "trendmicro_consumer",
"result": "Eicar_test_file",
"rca_factor": 0
},
{
"ignored": false,
"type": "av",
"classification": 0,
"factor": 0,
"name": "vba32",
"result": "EICAR-Test-File",
"rca_factor": 0
}
],
"rca_factor": 10
},
"story": [
{
"caption": "Description",
"content": "This file (SHA1: cf8bd9dfddff007f75adf4c2be48005cea317c62) is a text file. It was identified as a generic EICAR. There are no extracted files."
},
{
"caption": "Classification",
"content": "The file was classified as malicious, with the name Text.Format.EICAR, using TitaniumCore file format validation. One other scanner confirms the classification."
}
]
}
},
"request_id": "prq_x6fdiizbon6j3bsdvnpmwxsz2aan7fqd",
"request_time": "2022-09-21T17:24:33.105Z",
"response_time": "2022-09-21T17:24:34.007Z",
"status": "success"
}
Was this article helpful?