Activity Log
The Activity Log feature in Prompt Guard provides tracking of all service interactions. This enables logging, attribution, and accountability for your AI application activity.
When you enable Prompt Guard, its Activity Log is automatically activated. It captures critical details of each service call and allows you to track your application-specific events. This information is stored in Pangea's
Secure Audit Log , using a schema designed specifically to track and analyze AI application activity.The Activity Log page tracks all interactions within the Prompt Guard service, capturing:
- Timestamps
- Actor
- Input and output data
- Detections and contextual information
- Service configuration ID and recipe
- Authentication and authorization data
Learn more about configuring your Prompt Guard Activity Log in the General settings documentation.
Viewing logs
Logs can be accessed on the Prompt Guard Activity Log page in your Pangea User Console . You can also view a service usage summary on the Overview page.
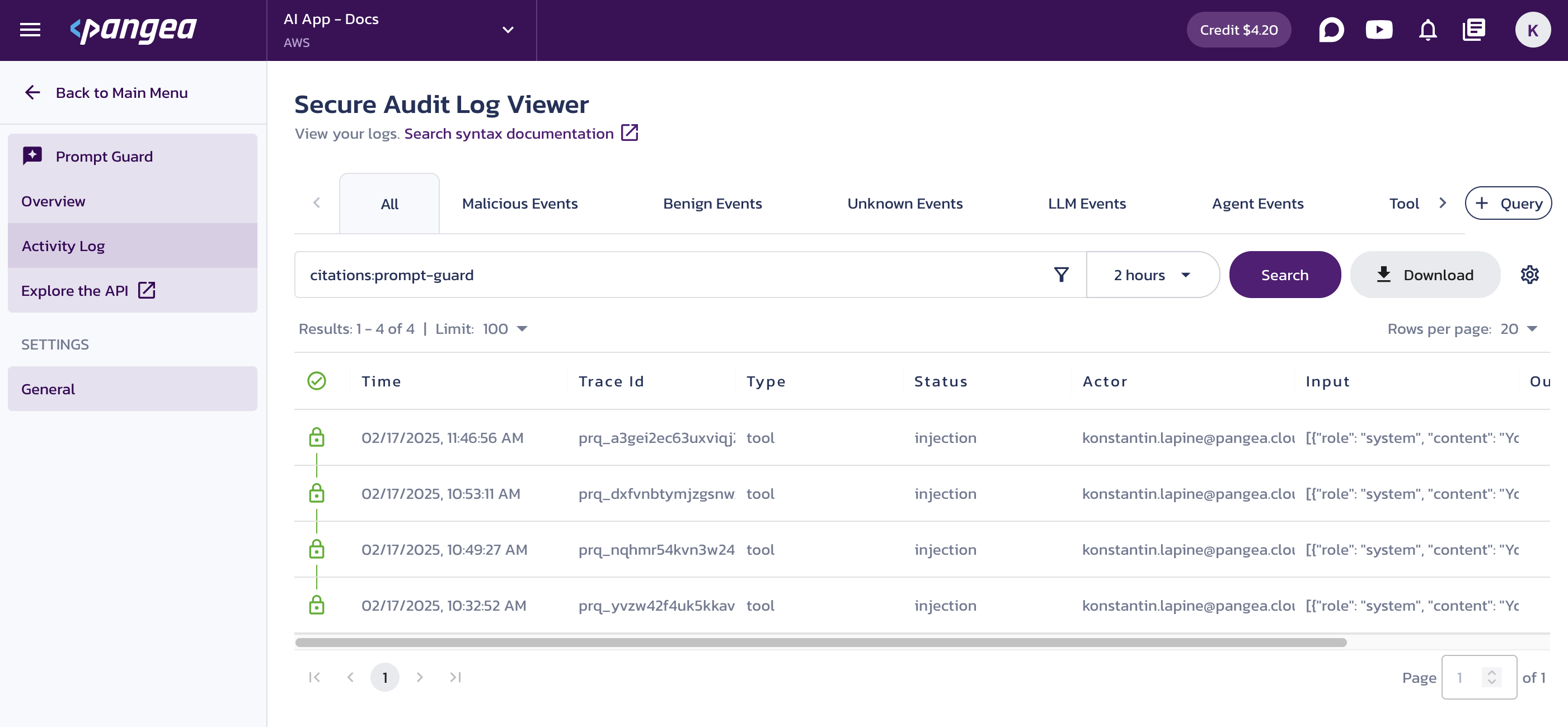
Quick search tabs
You can save your search criteria using the + Query button on the right. The saved query will appear as a tab at the top of the Secure Audit Log Viewer page. Several pre-defined searches are available in the Prompt Guard Activity Log by default.
Search bar
By default, the log viewer displays events from the past two hours.
To customize your search:
- Click the funnel icon to open the filter dialog, enter your criteria, and click Search. The search syntax appears in the search bar, and matching results display in the table.
- Place your cursor in the search bar to view a dropdown of available search parameters. Start typing to filter the list and use autocompletion to build your query.
- Enter your query manually. Learn more about the search syntax in the Secure Audit Log documentation.
Date range
All searches must include a time range, with the default set to the most recent two hours.
The date range selector next to the search button provides several options:
- Quick selections - Choose a relative range of 1, 7, or 30 days.
- Relative - Define a custom relative date range.
- Between - Search for log events between two specific dates.
- Before - Search for events that occurred before a specific date.
- After - Search for events that occurred after a specific date.
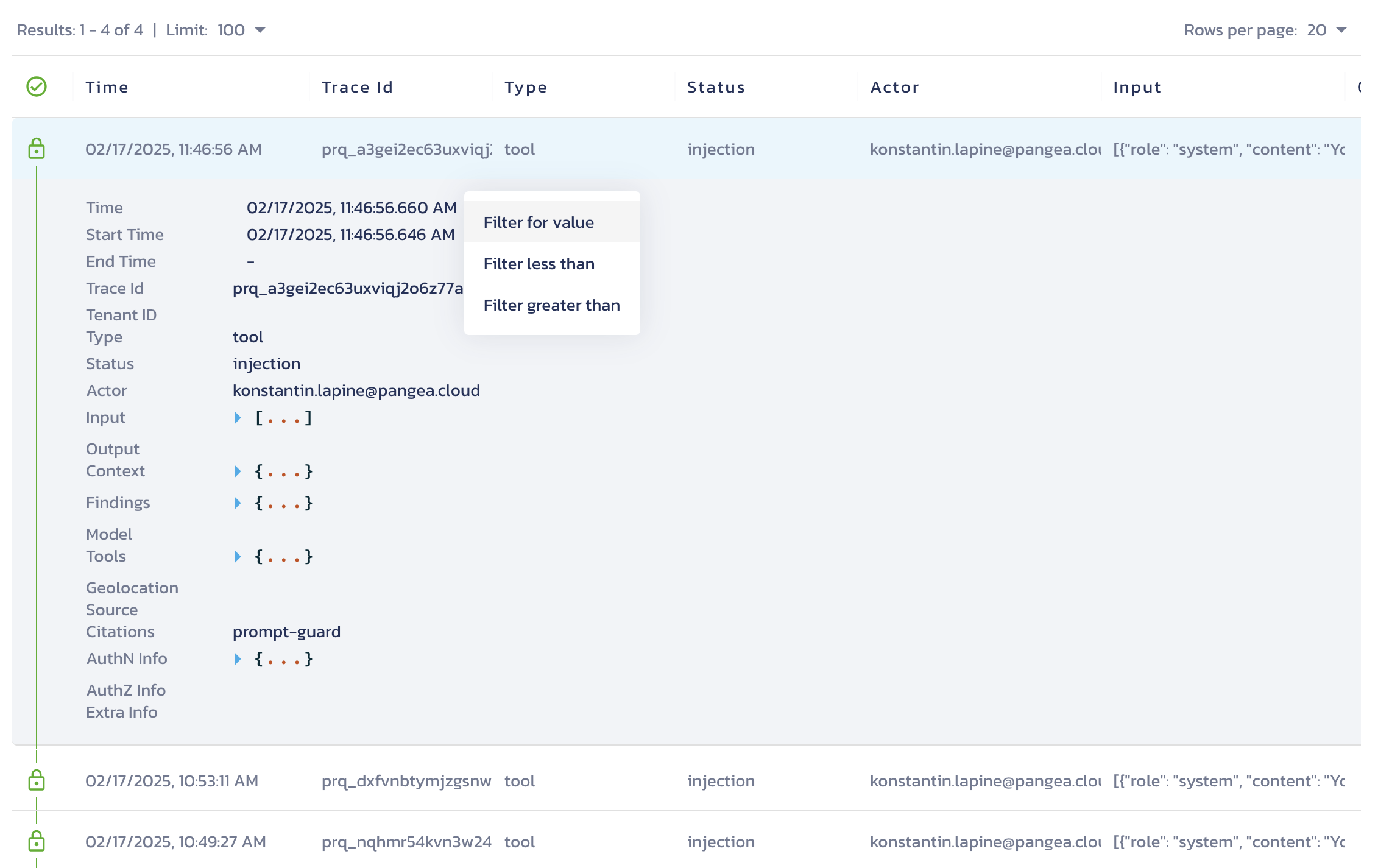
You can apply a time range filter directly from the log table. Hover over a timestamp in a result row or in the expanded details view, then click the ⨁ icon next to it to filter by that exact date or set it as the upper or lower limit of your range.
The log retention policy defines how long Pangea stores logs across different storage tiers and which logs remain searchable. For details, see the Secure Audit Log Retention policy documentation.
You can configure the Retention policy on the Secure Audit Log General Settings page in your Pangea User Console .
Results
Displayed fields
By default, the fields marked as Visible in the audit log schema are displayed as columns in the search results. To change which fields are displayed, click the gear button.
Learn more about configuring Prompt Guard Audit Log Schema in the General settings documentation.
Event details
To view all fields for an event, click its row in the search results. The row expands to show every event field, including those not currently visible in the table.
If a field (such as Old or New) contains JSON data, it displays as an interactive JSON tree.
Tamperproof information
Icons in the log viewer indicate tamperproof status for each record. Learn more about Tamperproofing in the Secure Audit Log documentation.
-
Lock icon
The lock icon shows that the membership proof for the log event is verified. Click the icon to open a pop-up with details for independently verifying the event:
-
Status - Possible statuses are Verified, Unverified, or Failed.
- Unverified - Indicates cached records that are not yet committed.
- Failed - Shows with a red lock icon.
-
Verification artifacts - Includes the message hash, membership proof, consistency proof, root hash, and a link to the published root hash.
-
Verification command - Provides a command you can run with Python SDK to verify the record's tamperproof status.
-
-
Green line
A vertical green line between lock icons indicates that the consistency proof for the two adjacent log events is verified.
Tamperproof icons appear asynchronously after search results return, as verification is performed.
Download logs
Use the Download button to save search results to a CSV file for analysis, sharing, archiving, importing into another audit logging service, or other purposes.
The download button may trigger a pop-up to verify that you want to download from the website. Some browsers block this pop-up, so you may need to allow pop-ups for the page. After that, you must confirm the download request before the download begins.
Was this article helpful?