Check for malicious files
Check your cloud app for malicious files using File Intel
The code samples below were created using the Pangea sample apps. If you want to follow along, check out the Pangea sample apps on GitHub:
Create a token
Expand for details
Create a token so that you can access the File Intel endpoints:
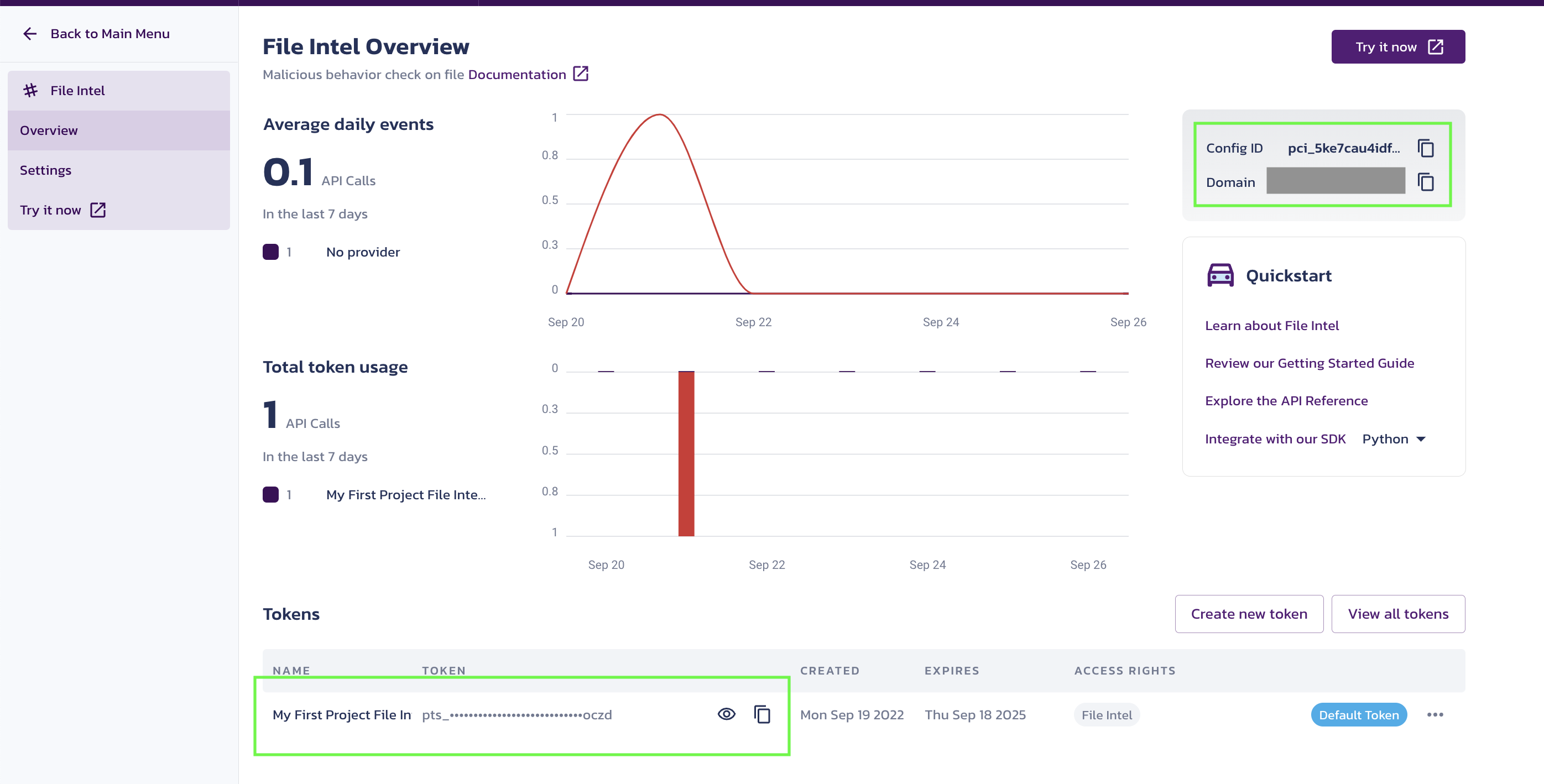
- Go to the Pangea Console and click File Intel in the left-hand navigation menu. The File Intel Overview page will appear.
- On the File Intel Overview page, you'll see a notification asking you to set a service token. Click Create new token toward the bottom right side of your screen.
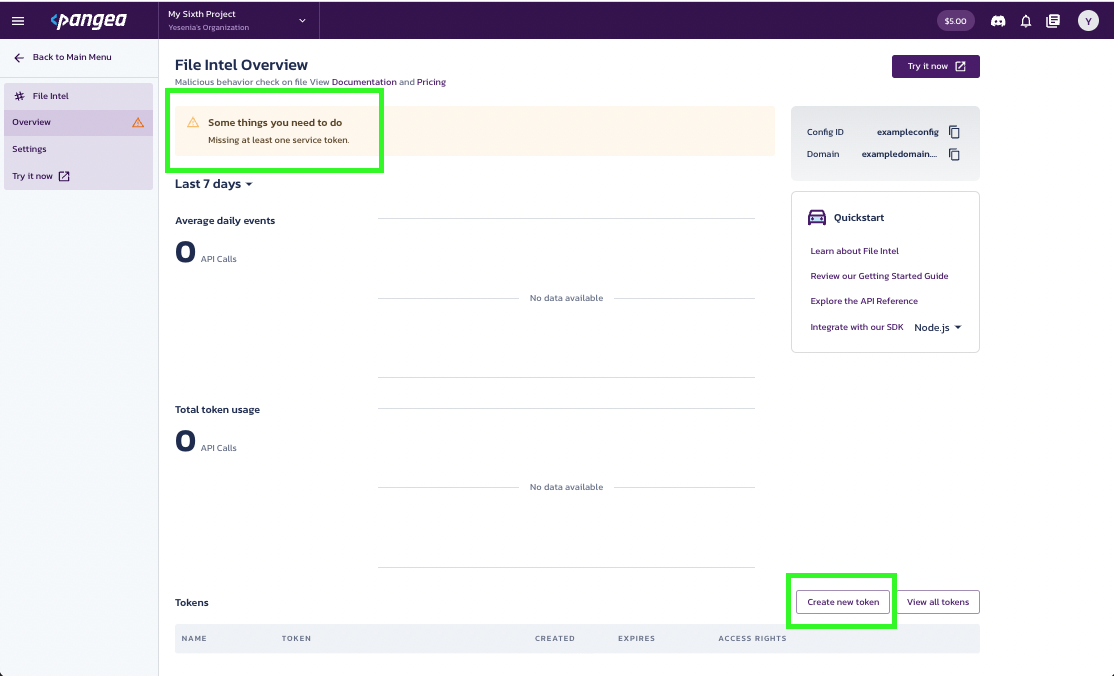
- You’ll be prompted to create a token. Enter a Token name and select an Expiration Date. You may also create a token for all Intel services, if you wish.
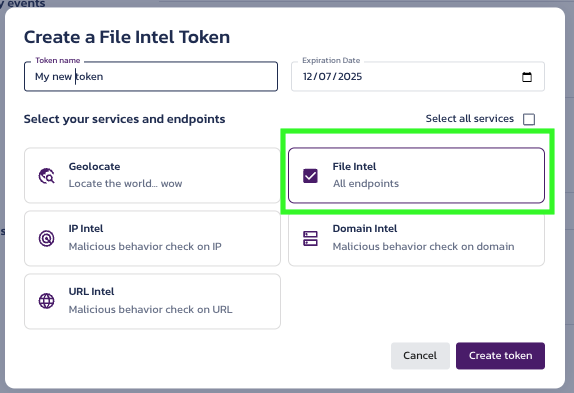
- Once configured, the token is available in the Tokens section of the File Intel Overview page.
Select your provider
Expand for details
Providers can be selected as default in the Pangea Console . Setting a provider as default in the Pangea Console means your API request calls will use this provider, unless another provider is specified as part of your API request.
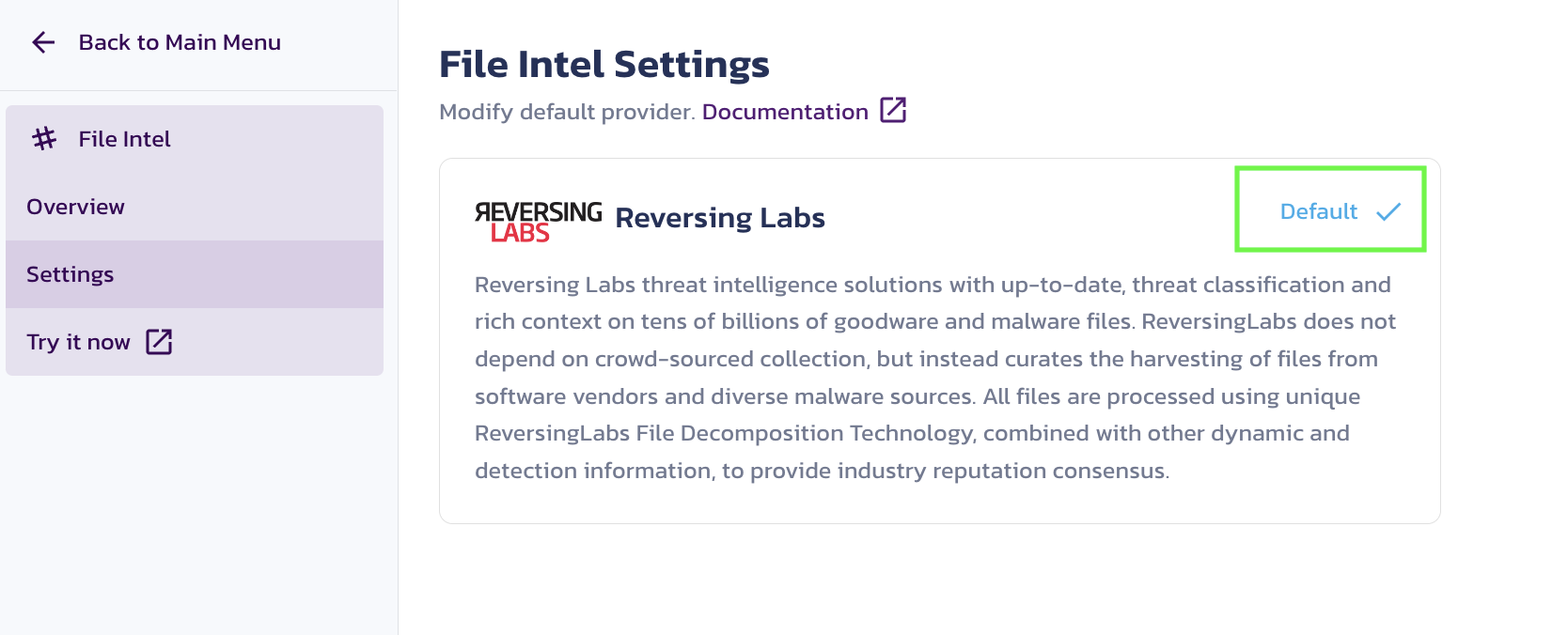
To select a provider as default for an API:
- Go to the Pangea Console
- On the left-hand navigation menu, select File Intel
- Go to Settings
- Click Set as default for your preferred provider
You can also select a provider and override the default provider by specifying their name in the provider field when making an API request to the /reputation endpoint. This is helpful if your default provider returns a verdict of Unknown and you want a second opinion from another provider.
Configure your app for communication with Pangea
For your app to communicate with the Pangea service, you must put the values of the following Configuration Details into the PANGEA_INTEL_TOKEN and PANGEA_DOMAIN environment variables:
tokendomain
These variables are created when you enable File Intel and can be found in the Overview section under File Intel.
Set environment variables
To set each variable in bash:
export PANGEA_DOMAIN="yourServiceDomain"
export PANGEA_INTEL_TOKEN="yourAccessToken"
A hash is calculated
The ways you acquire a file hash may vary. For example, you might:
- Use a reporting tool that generates a hash for suspicious files
- Calculate a hash using your app
If you add hash calculation functionality to your app, it may look something like this:
import hashlib
def main():
myfile = open('/path/to/file', 'rb')
print(hashlib.sha256(myfile.read()).hexdigest())
if __name__ == '__main__':
main()
Your result will look something like this:
% python ~/scratch/hash.py
142b638c6a60b60c7f9928da4fb85a5a8e1422a9ffdc9ee49e17e56ccca9cf6e
Submit hash to the File Intel service
At this point, your app submits the hash to the File Intel service. The code in your app might look something like this:
import os
import pangea.exceptions as pe
from pangea.config import PangeaConfig
from pangea.services import FileIntel
token = os.getenv("PANGEA_INTEL_TOKEN")
domain = os.getenv("PANGEA_DOMAIN")
config = PangeaConfig(domain=domain)
intel = FileIntel(token, config=config)
def main():
print("Checking file...")
try:
response = intel.reputation(
hash="142b638c6a60b60c7f9928da4fb85a5a8e1422a9ffdc9ee49e17e56ccca9cf6e",
hash_type="sha256",
)
print(f"Response: {response.result}")
except pe.PangeaAPIException as e:
print(f"Request Error: {e.response.summary}")
if e.errors:
for err in e.errors:
print(f"\t{err.detail}")
print("")
File Intel API sends a response
After your app submits a hash file to the File Intel service, you will receive the JSON response below.
In this instance:
- The
verdictreturned asmalicious - Additional
rawdata (from the provider specified in the API request) was returned because therawfield was set totrue
{
"request_id": "prq_37fvd6ofo2sz3wbvmaqrb4bmzrzcuhxh",
"request_time": "2022-09-27T21:23:19.682Z",
"response_time": "2022-09-27T21:23:20.258Z",
"status": "Success",
"summary": "Hash was found",
"result": {
"data": {
"category": ["Trojan"],
"score": 100,
"verdict": "malicious"
},
"parameters": {
"hash": "142b638c6a60b60c7f9928da4fb85a5a8e1422a9ffdc9ee49e17e56ccca9cf6e",
"hash_type": "sha256",
"provider": "reversinglabs",
"raw": true,
"verbose": true
},
"raw_data": {
"rl": {
"entries": [
{
"classification": {
"family_name": "BoxerSms",
"is_generic": false,
"platform": "Android",
"type": "Trojan"
},
"first_seen": "2012-08-30T09:50:00",
"last_seen": "2021-07-17T08:24:17",
"query_hash": {
"sha256": "142b638c6a60b60c7f9928da4fb85a5a8e1422a9ffdc9ee49e17e56ccca9cf6e"
},
"reason": "antivirus",
"scanner_count": 29,
"scanner_match": 17,
"scanner_percent": 58.620689392089844,
"status": "MALICIOUS",
"threat_level": 5,
"threat_name": "Android.Trojan.BoxerSms",
"trust_factor": 5
}
]
}
}
}
}
Understand and review the results
The API response sent by File Intel includes various fields and values; however, the ones listed below give you the most information about the disposition of a file hash. To learn about more response fields, visit the File Intel API Reference.
verdict | The verdict normalized categorization as interpreted by the data returned by the third party provider. There are four possible verdicts:
|
score | The normalized score as interpreted by the data returned by the third party provider. Scores are associated with the verdict values listed above:
|
summary | A summary of the various categories associated with a file hash, which help illustrate why a file hash received a particular verdict. |
category | Indicates the category of file associated with the file hash (e.g. Adware, Malware). This field may return more than one category and may, at times, not be populated. |
raw | Raw data returned by the provider you specified in the API request. You
can investigate the raw data if its meaningful to your use case or if
you want to supply it to your users. You must set the |
Based on the File Intel API response, it’s evident that the file hash you submitted was Malicious.
Decide what to do with file
You decide how to respond and/or communicate with your users once a file's reputation becomes evident. Here are some suggestions:
- If the file is malicious, delete it and display a message to the user.
- If a file is non-malicious, allow it and save it.
In this case, the file will be deleted and the following message will be displayed to the user:
“The file you uploaded was determined to contain malicious content, and has been deleted.”
Was this article helpful?