Multiple Service Configurations
Learn how to create additional Secure Audit Log configurations and use tokens with access to multiple service configurations
The Secure Audit Log service supports multiple configuration settings within a single project. Each configuration is independent and operates in isolation from others.
By using multiple configurations, you can address different requirements and scenarios within the same Pangea project. This includes customizing log retention periods, log event fields, redact policies, and other settings. You can create separate access tokens for different configurations or use the same token across multiple configurations.
Create additional configurations
-
Navigate to the
Secure Audit Log page in the Pangea User Console. -
Click on the configuration drop-down at the top of the left-hand sidebar (where the currently selected configuration name is displayed) and select + Create New.
Alternatively, you can go to the Settings tab, click Audit Log Schema, and follow the Create a new configuration link.
This will open the configuration multi-stage modal. Since you've already enabled the service, the modal will display the following two steps for a new configuration:
Tokens for multiple service configurations
When creating a configuration, you can use the Extend an existing token dropdown to grant the token access to multiple Secure Audit Log configurations.
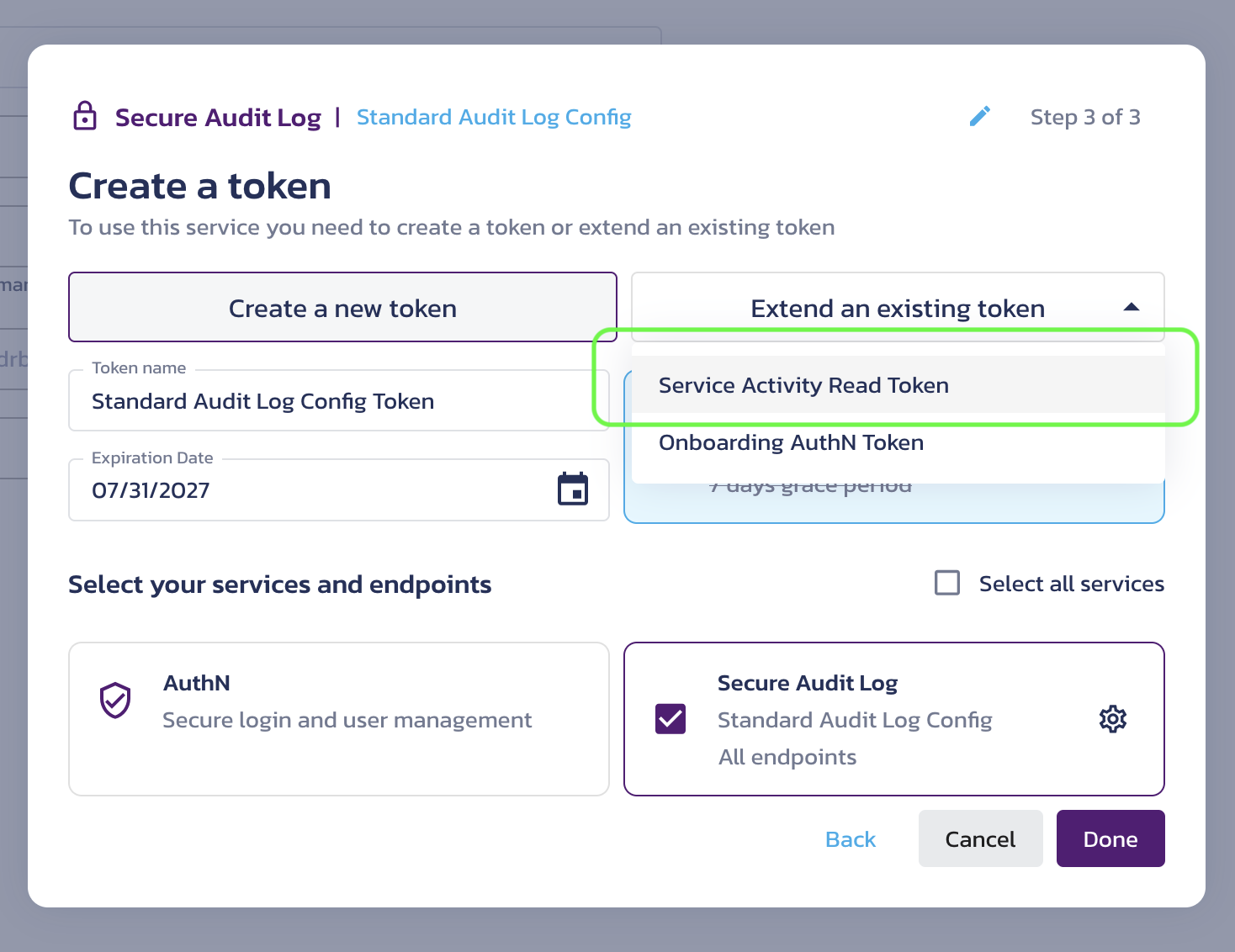
If you use the same token for multiple service configurations, the token alone is not sufficient to determine which configuration you are requesting. In this case, you MUST specify a configuration ID when calling the service APIs. Otherwise, you will receive an AmbiguousConfigID error.
Example request
You can use the Secure Audit Log /v1/log API endpoint to save a single event.
Send your request to your Pangea project domain and authorize it with a token that has access to your Secure Audit Log configuration. To avoid ambiguity, include the configuration ID along with the event data in the request parameters.
Since these parameters are relatively stable across requests, you can save them as environment variables:
export PANGEA_DOMAIN="aws.us.pangea.cloud"
export PANGEA_AUDIT_TOKEN="pts_u7ivbl...pfhqlx"
export PANGEA_AUDIT_CONFIG_ID="pci_kg4zyf...vddgwh"
Make the request directly to the Secure Audit Log APIs or use one of the available SDKs:
pip3 install pangea-sdk
or
poetry add pangea-sdk
import os
import pangea.exceptions as pe
from pangea.config import PangeaConfig
from pangea.services import Audit
domain = os.getenv('PANGEA_DOMAIN')
token = os.getenv('PANGEA_AUDIT_TOKEN')
config_id = os.getenv('PANGEA_AUDIT_CONFIG_ID')
config = PangeaConfig(domain=domain)
audit = Audit(token, config=config, config_id=config_id)
def main() -> None:
message = 'Hello, World!'
try:
log_response = audit.log(message=message, verbose=True)
assert log_response.result
print(f'envelope: {log_response.result.envelope}')
except pe.PangeaAPIException as e:
print(f'Request Error: {e.response.summary}')
for err in e.errors:
print(f'\t{err.detail} \n')
if __name__ == '__main__':
main()
envelope: event={'message': 'Hello, World!'} signature=None public_key=None received_at=datetime.datetime(2024, 8, 1, 2, 36, 32, 632466, tzinfo=TzInfo(UTC))
Was this article helpful?