Secure Audit Log
Meet your compliance requirements by recording activity to a tamperproof audit log. Scales to even the most demanding retention and recall requirements.
A secure audit log is a critical component of any system that requires accountability and transparency by providing an accurate and secure record of all system events.
This guide provides a self-sufficient code example for making a request to the Secure Audit Log APIs that you can try in one of the supported environments.
Get a free Pangea account and enable the service
- Sign up for a free Pangea account .
- After creating your account and first project, skip the wizards to access the Pangea User Console.
- Click Secure Audit Log in the left-hand sidebar to enable the service.
- In the enablement dialogs, accept defaults, click Next, then Done, and finally Finish to open the service page.
- On the Secure Audit Log Overview page, note the Configuration Details, which you can use to connect to the service from your code. You can copy individual values by clicking on them.
- Follow the Explore the API links in the console to view endpoint URLs, parameters, and the base URL.
Connect to the Secure Audit Log service
Your application can use the SaaS domain to send API requests and a service token to authorize them. Both parameters are available in the service Configuration Details on the Overview page in your Pangea User Console. You can make them available to your application, for example, by assigning them to environment variables:
export PANGEA_DOMAIN="aws.us.pangea.cloud"
export PANGEA_AUDIT_TOKEN="pts_qbzbij...ajvp3j"
Learn more about how to authorize access to the service in the API Credentials documentation.
Add audit logging to your app
In the following examples, you will submit an event to the Secure Audit Log API and receive a response confirming that the log was saved. The event data will appear in your Pangea User Console, where you can view and search your logs, check the integrity of your logs, and forward them to a SIEM.
The steps below will walk you through the basics of integrating Secure Audit Log in a Python app. For more in-depth information and additional examples:
- Visit the Python SDK documentation.
- Check out the SDK GitHub repo .
- Explore the service APIs .
Install the Pangea SDK
pip3 install pangea-sdk==5.5.0
or
poetry add pangea-sdk==5.5.0
or
uv add pangea-sdk==5.5.0
Instantiate the Secure Audit Log service client
import os
from pydantic import SecretStr
from pangea.config import PangeaConfig
from pangea.services import Audit
domain = os.getenv("PANGEA_DOMAIN")
token = SecretStr(os.getenv("PANGEA_AUDIT_TOKEN"))
config = PangeaConfig(domain=domain)
client = Audit(token=token.get_secret_value(), config=config)
# ...
Log events
import os
from pydantic import SecretStr
from pangea.config import PangeaConfig
from pangea.services import Audit
domain = os.getenv("PANGEA_DOMAIN")
token = SecretStr(os.getenv("PANGEA_AUDIT_TOKEN"))
config = PangeaConfig(domain=domain)
client = Audit(token=token.get_secret_value(), config=config)
try:
log_response = client.log(
message="Security updated",
action="Off",
actor="dennis.nedry@ingen.com",
target="Visitor center",
verbose=True,
)
print(f"Hash: {log_response.result.hash}")
print(log_response.result.envelope.event)
except Exception as e:
print(f"Error: {e}")
Hash: c6bd846e73beadd436e19e77d396728ac5c3c4ee88ba93c52f4368603b0c6251
{'message': 'Security updated', 'actor': 'dennis.nedry@ingen.com', 'action': 'Off', 'target': 'Visitor center'}
View logs
In the Pangea User Console, navigate to Secure Audit Log > View Logs to see the event you just logged.
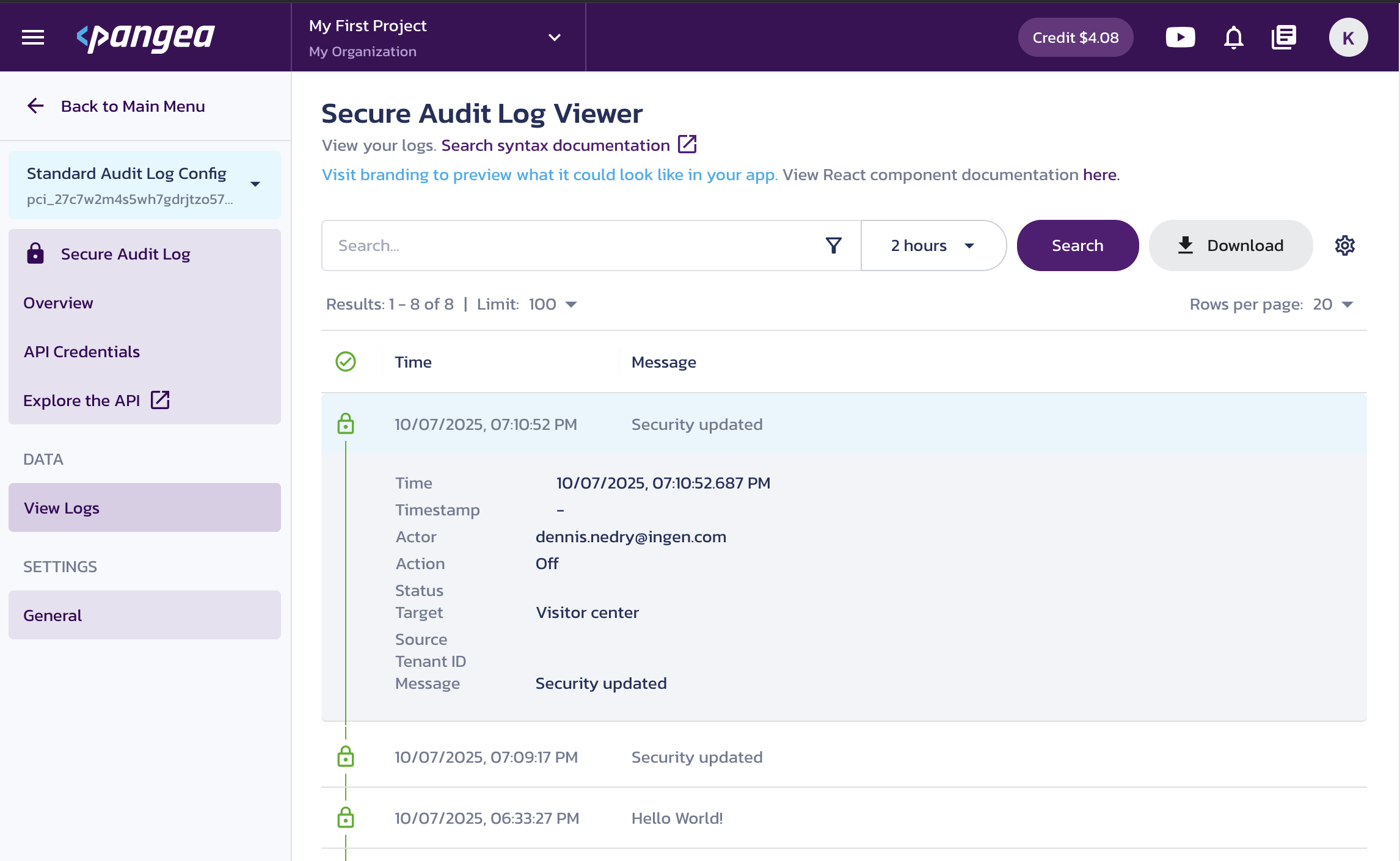
Next steps
-
Learn more about Secure Audit Log capabilities in the service overview documentation.
-
This example shows how an event can be saved in the default Secure Audit Log configuration schema. Learn how to create and use multiple service configurations tailored for specific use cases within your application.
-
Explore the Secure Audit Log APIs in the interactive API Reference documentation.
-
Learn how to manage your Pangea account and services in the Admin Guide.
Was this article helpful?