Splunk
You can configure audit logs to be forwarded to Splunk using the HTTP Event Collector (HEC) protocol, allowing you to consolidate Pangea logs with your existing Splunk data for centralized analysis and reporting.
Enable HTTP Event Collector in Splunk Web
Use the following resources to assist with the HTTP Event Collector (HEC) setup:
Set up log forwarding
-
Select an audit schema.
On the Secure Audit Log service page in your Pangea User Console , use the schema selector in the top-left to choose the configuration you want to forward to Splunk.
-
Click General in the sidebar to open the settings for the selected schema.
-
Under Audit Log Forwarding, toggle the control in the top-right to Enabled.
-
Set Logging Service to Splunk.
-
For Event URL, enter the full URL for sending events (e.g.,
https://<myhost>.<tld>/services/collector/event). -
(Optional) In the Index field, specify the Splunk index to include in the HEC payload. This can also be set in the HEC token settings.
-
(Optional) Configure Enable Indexer Acknowledgment only if this feature is enabled in your Splunk HEC settings:
- Acknowledge URL – The URL used for acknowledgment verification, typically in the format
https://<myhost>.<tld>/services/collector/ack. - Channel ID – Required for indexer acknowledgment. Generate a value using
uuidgenor a similar tool.
- Acknowledge URL – The URL used for acknowledgment verification, typically in the format
-
Click the Store HEC Token button.
- In the New Secret dialog, enter the HEC token from your Splunk setup in the Secret field.
- Click Done.
-
(Optional) In the Provider certificate to use self-signed TLS input, upload the public certificate of your private CA if you're using a self-signed or privately issued TLS certificate. This is not required if the certificate is issued by a trusted public Certificate Authority (CA).
-
Click Save to apply the configuration.
-
Click Test forwarding configuration to validate the setup.
If successful, the following message will appear:

In Splunk, you should see a message forwarded by the Secure Audit Log service:
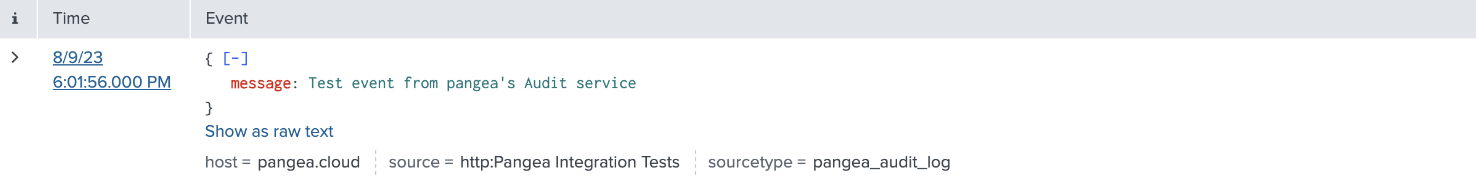
If the configuration test fails, an error message will appear at the top of the screen. For example, the following message indicates a certificate misconfiguration:

Was this article helpful?