CrowdStrike Next-Gen SIEM
You can configure audit logs to be forwarded to CrowdStrike Next-Gen SIEM using the HTTP Event Collector (HEC) protocol. This allows you to centralize Pangea logs alongside other CrowdStrike telemetry for unified threat detection, monitoring, and response.
Configure a connector
In your CrowdStrike Falcon console, follow the instructions in Step 1: Configure and activate the Pangea AI Guard data connector in the
HEC/HTTP Event Connector guide.For example:
-
Navigate to the Data connections page under Next-Gen SIEM >> Data onboarding in your CrowdStrike Falcon console.
-
Click Add connection in the list of connections.
-
In the Product filter, select HEC.
-
Click HEC / HTTP Event Connector in the list.
-
Click Configure.
-
On the Add new connector page, enter Data source, Connector name, and Description.
-
Under Parser details, select a parser.
Pangea offers a CrowdStrike Next-Gen SIEM parser designed to process events from the
AI Guard Activity Log , which is enabled by default when the AI Guard service is activated.Select PangeaAIGuardParser if you're forwarding AI Guard activity logs to CrowdStrike.
-
Accept the terms and conditions, then click Save.
-
On the connector details page, click Generate API key.
-
Copy the API key and API URL. You will use these values to configure log forwarding in the Secure Audit Log service.
Set up log forwarding
-
Select an audit schema.
On the Secure Audit Log service page in your Pangea User Console , use the schema selector in the top-left to choose the configuration that matches your CrowdStrike parser.
To forward AI Guard activity logs, select
AI Activity Audit Log Schema. -
Click General in the sidebar to open the settings for the selected schema.
-
Under Audit Log Forwarding, toggle the control in the top-right to Enabled.
-
Set Logging Service to CrowdStrike Next-Gen SIEM.
-
For Event URL, enter the API URL from your CrowdStrike connector.
-
Click the Store HEC Token button.
-
In the New Secret dialog, enter the API key from your CrowdStrike connector in the Secret field.
-
Click Done.
-
Click Save to apply the configuration.
-
Click Test forwarding configuration to validate the setup.
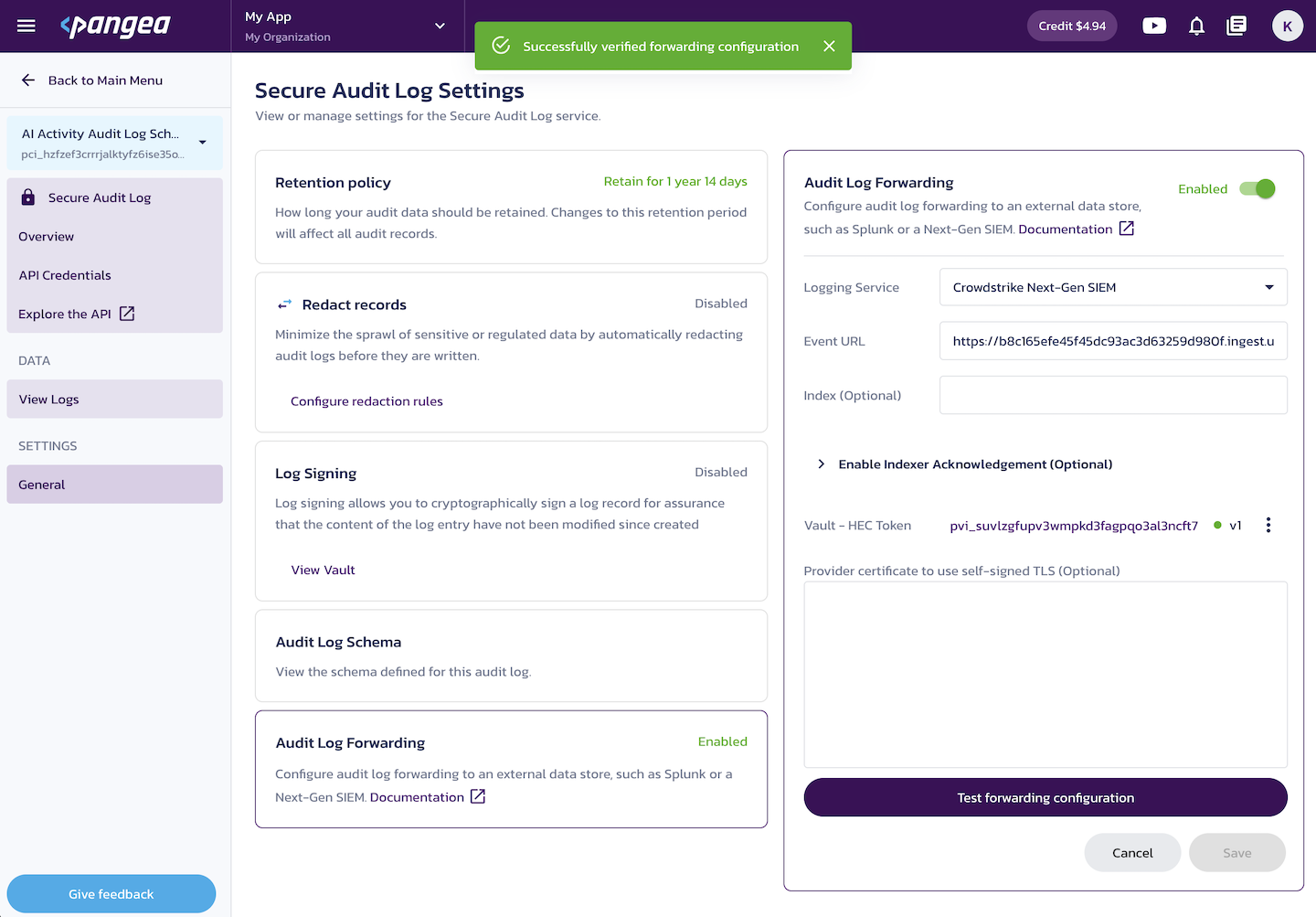
A failed test displays an error message, for example:

To generate real events, return to the service list, open the AI Guard service page, and under Recipes, use the Sandbox feature to send a sample input.
After a few minutes, you should see the forwarded events in your CrowdStrike Falcon console under Next-Gen SIEM >> Advanced event search.
The following optional fields are not applicable when using the CrowdStrike Next-Gen SIEM connector:
- Index
- Indexer Acknowledgment
- Provider certificate to use self-signed TLS
Next steps
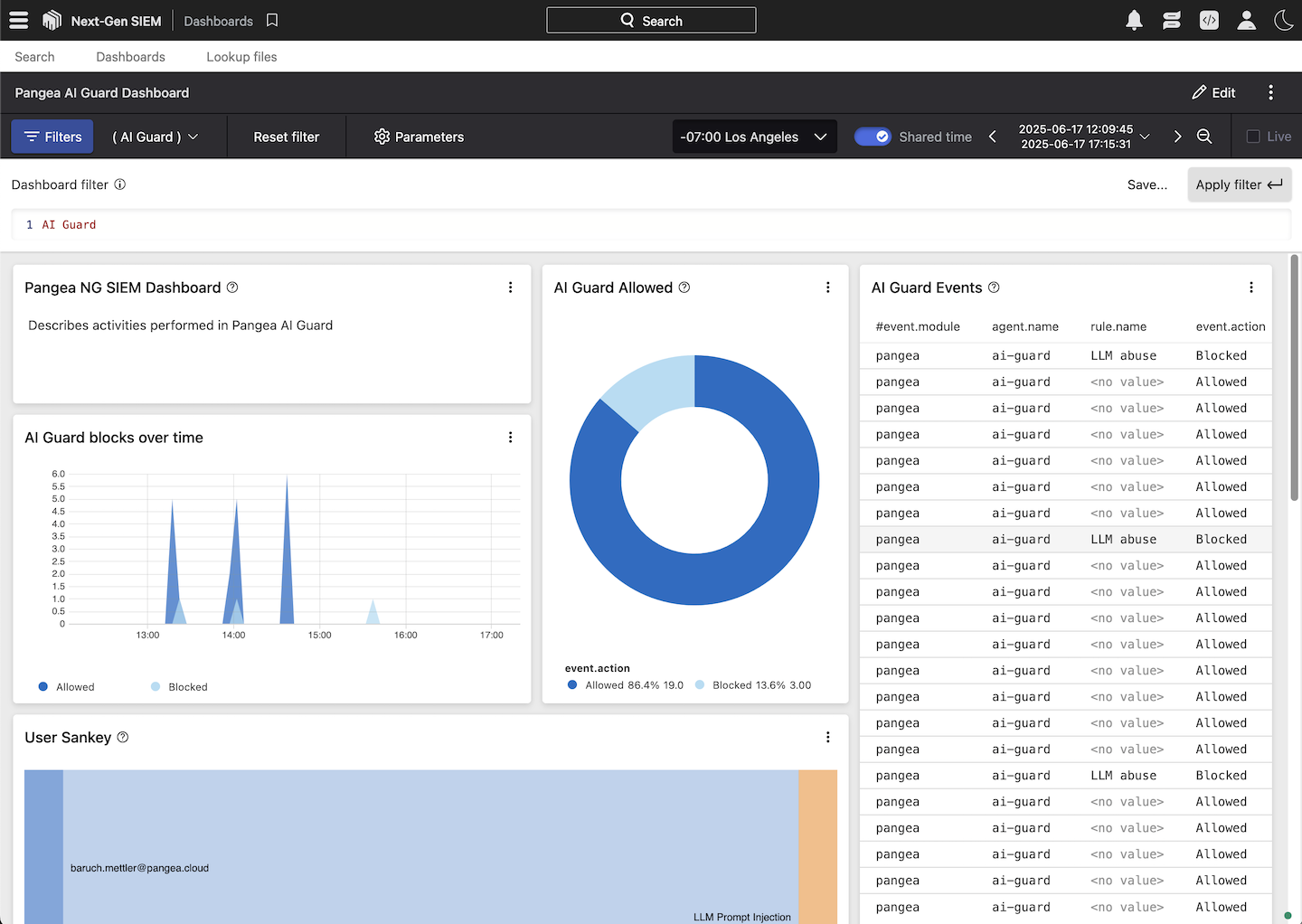
To visualize log data forwarded from Pangea to CrowdStrike Next-Gen SIEM, use the prebuilt Pangea dashboards available on GitHub . You can import these dashboards into your CrowdStrike Falcon console by following the instructions in the repository README.
Was this article helpful?